Identification, Authentication, Authorization, and Accountability

Identification
Identification, the crucial process of using various data and information to establish a person's or subject's identity, is the cornerstone of the access control process. It's the initial step where a user or system presents credentials or attributes that assert their identity. This process is vital as it helps to recognize an individual using data such as their name, username, user IP address, employee number, social security number, tax ID, social media handle, and other relevant information.
When attackers gain access to personal identification, the consequences can be severe. They can impersonate legitimate users, leading to data breaches and unauthorized transactions. With compromised identification, attackers can elevate their access rights, potentially gaining administrator-level access and manipulating system settings, data, and access controls. They can also perpetrate fraud by stealing funds or services by impersonating the rightful owner of the identity. Knowing someone's identifier can allow attackers to craft targeted phishing or social engineering attacks, tricking victims into revealing more sensitive information or installing malicious software. Additionally, attackers might use stolen identification to disrupt services by overwhelming a system with requests as part of a Denial of Service attack or altering system configurations. The compromise of identification could undermine trust in a system's security, affecting user confidence and potentially causing reputational damage to the organization.

Authentication
Authentication means proof that a subject (like a person) or an object (like an application) is who they claim to be through three methods. These authentication methods are the following:
- "Something you know" would be like a password, PIN, and the answers to security questions. Hackers typically attack knowledge factors since they are less challenging than the other authentication methods. Knowing this, we can ensure that knowledge-based authentication information is more difficult to crack. For instance, we can increase the complexity and number of characters of our passwords to prevent cyber criminals from breaking them and selling that information on the dark web, which is illegal.
- "Something you have" is another authentication method that includes professional IDs, smart cards, hardware tokens (similar to thumb drives in appearance), and browser cookies. A person or subject uses a tangible or intangible item "they have" to authenticate their identity.
- "Something you are" includes a person's physiological characteristics used to authenticate. Biometrics is an example of using physiological characteristics to authenticate. Unique fingerprint patterns and the complex pattern of ridges and furrows inside the human iris are examples of physiological characteristics used in biometrics. Behavioral characteristics are also used in the authentication process to establish a baseline to identify suspicious changes by studying a person's behavioral pattern. Voice pattern recognition is an example of a behavioral characteristic used in biometric authentication.
Authorization
The Principle of Least Privilege is a security principle that focuses on granting access permissions to only those subjects who require them to perform their duties. By adhering to this principle, we can prevent subjects from intentionally or unintentionally compromising information that may negatively affect an organization's financial status and human lives. It is crucial to enforce this principle at all times, particularly when granting new hires access to resources or transitioning personnel to new roles.
The Need-to-Know principle requires that a person be granted access to information and data only if it is necessary to perform a specific duty, even if the individual already has access permissions.
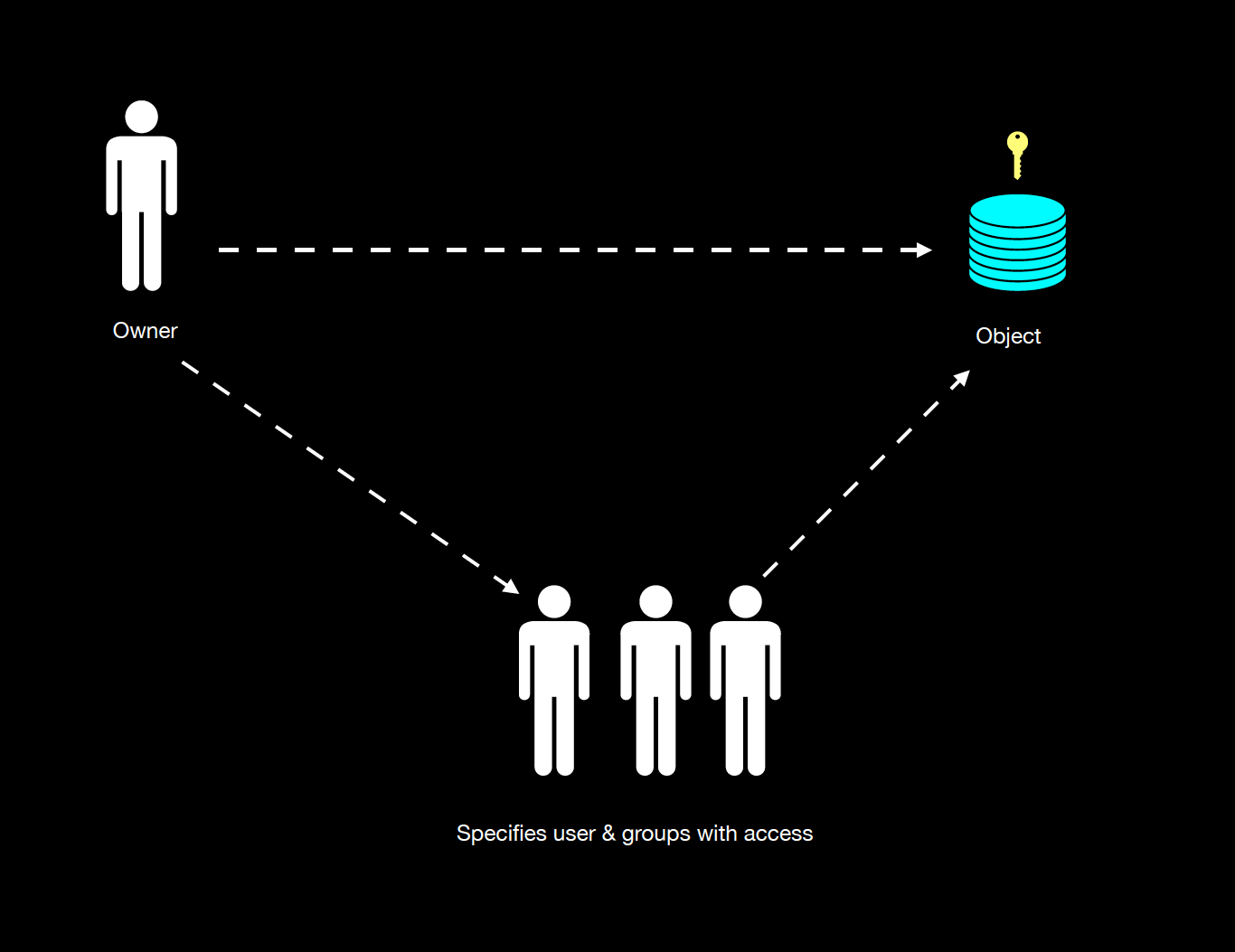
Discretionary Access Control (DAC)
Discretionary Access Control is used when availability is critical. Since this access control type is identity-based, the object owner or system decides to assign object access at their discretion to a specific subject. The resource owner can use this access control type to grant access to particular groups or users who need it to ensure access to resources that must be available to them when performing duties and responsibilities. While DAC is a distributed model that is useful when no central authority has sufficient information to perform access control decisions, its flexibility and decentralized nature can pose a security risk. For instance, a centralized IT department may not know who needs access to a specific file or folder on Google Drive, but the file or folder's owner knows whom to grant access to collaborate. However, enforcing consistency becomes more complicated when a large group of data owners make access control decisions, including the ability to make permission changes, which insider threats can exploit.
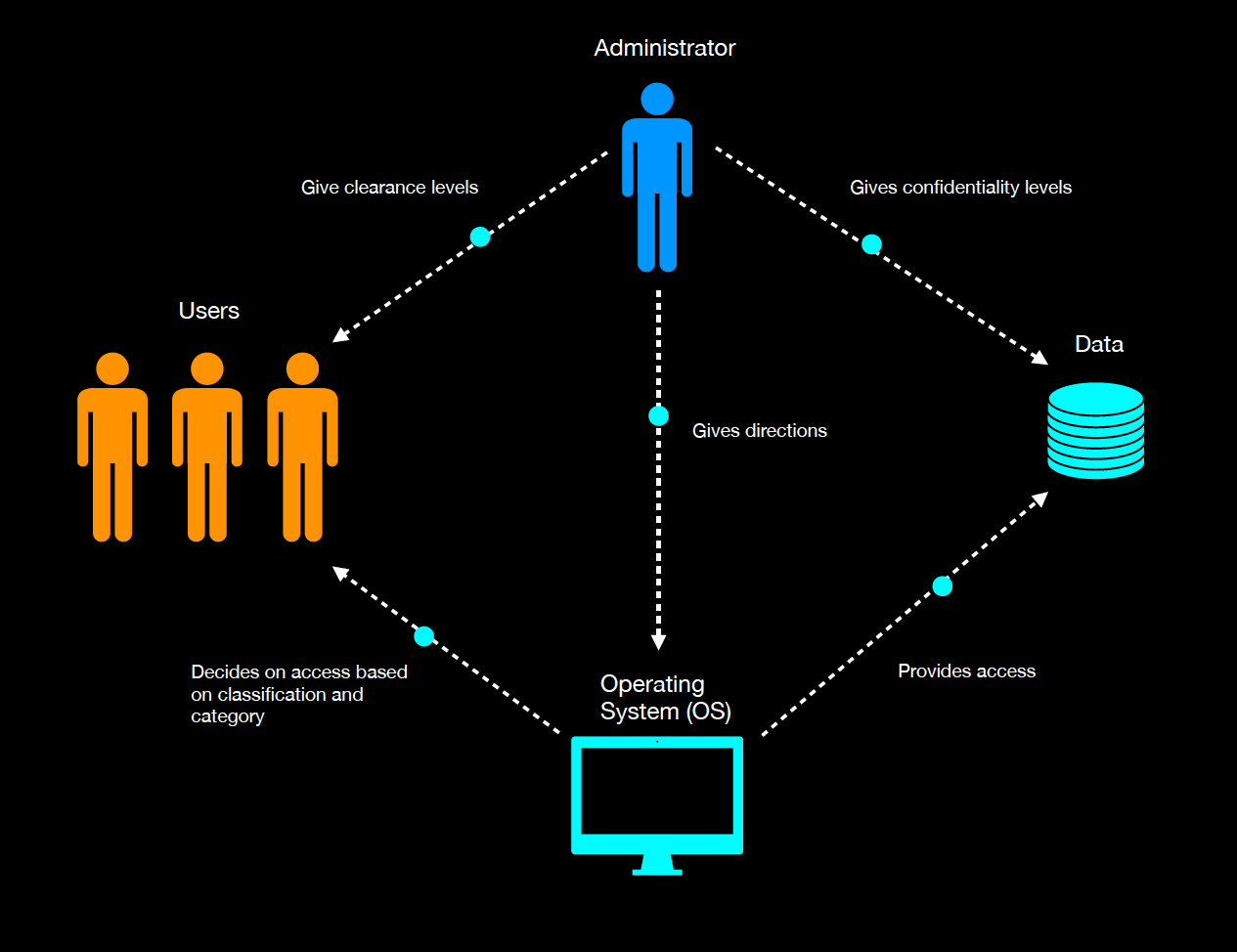
Mandatory Access Control (MAC)
Often used in the government and military, critical infrastructure (e.g., power plants, financial institutions, and healthcare systems), and corporate environments where sensitive data needs to be tightly controlled, Mandatory Access Control is used when confidentiality is vital. This type of access control is rules-based and policy-driven, ensuring only administrators can change rules and policies. Under MAC, access permissions are pre-determined for all users and are centrally managed for ease of administration, meaning access control is not at the discretion of data owners. Still, it is enforced systematically where the data owner is responsible for assigning the appropriate security label to an object (e.g., files, databases, or devices) and a subject, such as users or processes, is assigned a security clearance so when a subject attempts to access an object, the system checks the subject's clearance against the object's classification label to determine access permissions.
One standard MAC model is the Bell-LaPadula Model, which focuses on maintaining data confidentiality and enforces rules to prevent information flow from higher to lower security levels. Another standard MAC model is the Biba Model, which focuses on data integrity and enforces rules to prevent information flow from lower to higher integrity levels.
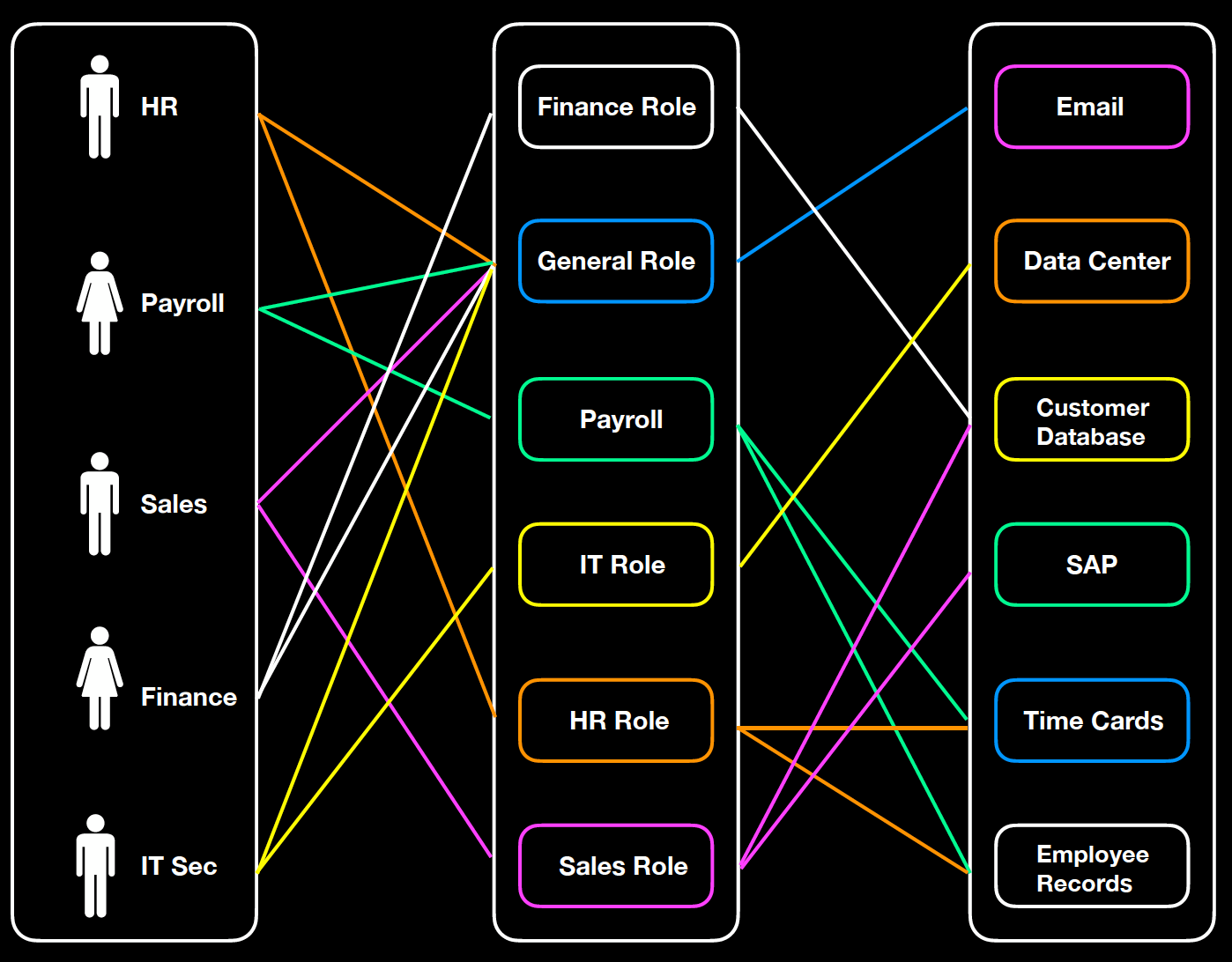
Role-Based Access Control (RBAC)
Role-Based Access Control is used when data integrity preservation is critical or most important. It's a policy-neutral access control mechanism defined based on roles and privileges. RBAC is the most effective access control to help prevent any change to data and information, which could cause significant financial loss and negatively impact people's lives. RBAC must be used when there needs to be a clear separation between organizational departments, teams, roles, and the corresponding data and information each is authorized to access. In RBAC, roles are first identified within an organization. For instance, "Finance," "HR," and "Sales" are roles defined by a company. Each of these roles is assigned permissions, such as "read," "write," "execute," and other access rights required to perform specific duties and access particular resources (objects). These roles are then assigned to users based on their job functions and responsibilities. When a user (subject) attempts to access a resource, the system checks the user's roles and the permissions associated with those roles to determine if access should be granted.
Attribute-Based Access Control (ABAC)
Being more flexible, dynamic, and risk-based than other access control models, the Attribute-Based Access control has a mechanism where access to an object or resource is granted or denied to a subject based on the subject, object, and environment's attributes when evaluated against a policy. For instance, a stateful multi-layer firewall can allow incoming traffic from the internet, granting it access to a specific endpoint if it meets the policy specifying that incoming internet traffic that corresponds to a previously established communication session by one particular endpoint will be allowed entry into the private network. Another example would be a finance manager attempting to access sensitive files on the company's private network outside of regular working hours from an unrecognized device in a foreign country will be denied access since object and environmental attributes do not meet policy specifics, even though the subject's attributes, which in this case are his user credentials and multi-factor authentication, meets some of a policy's requirements.
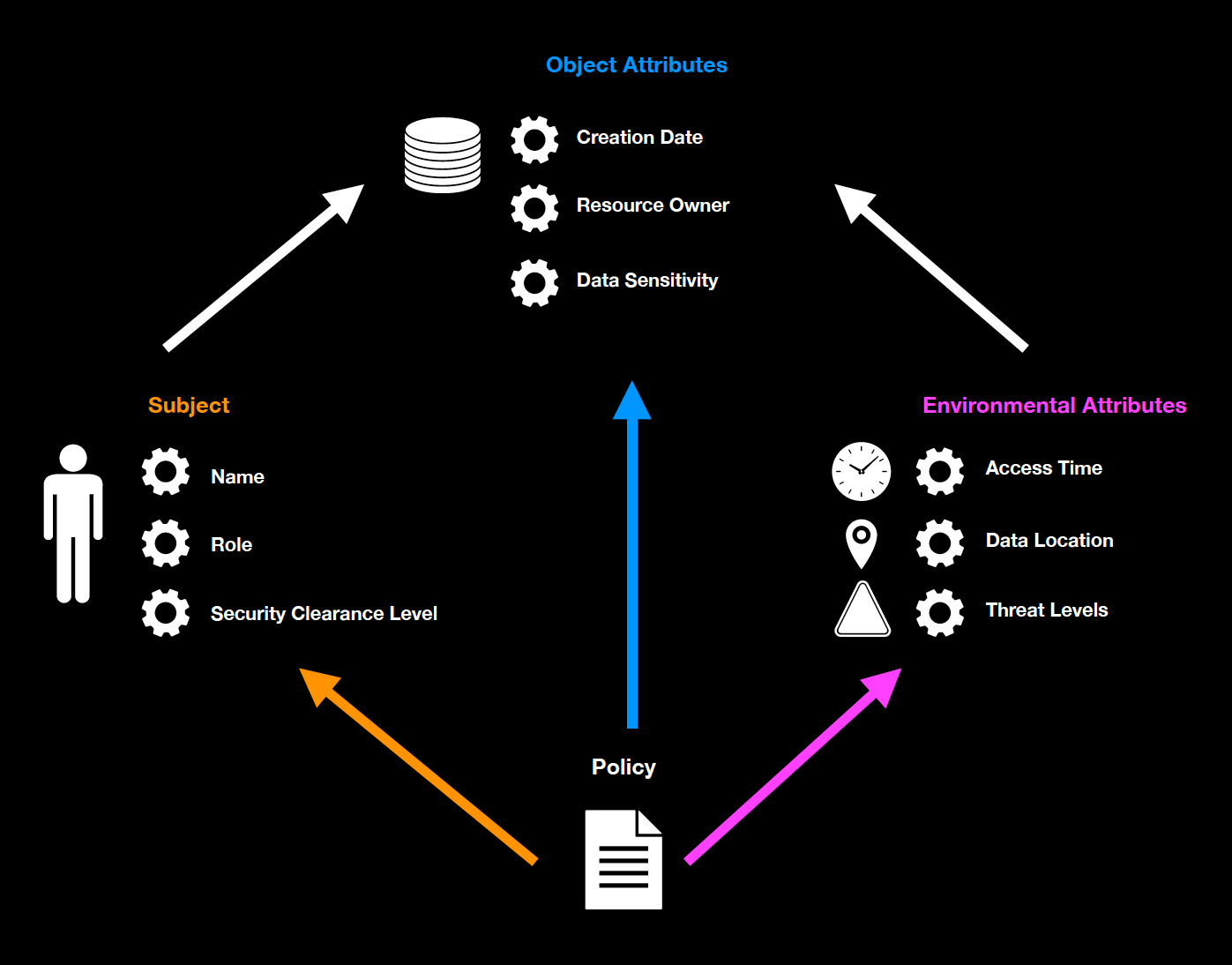
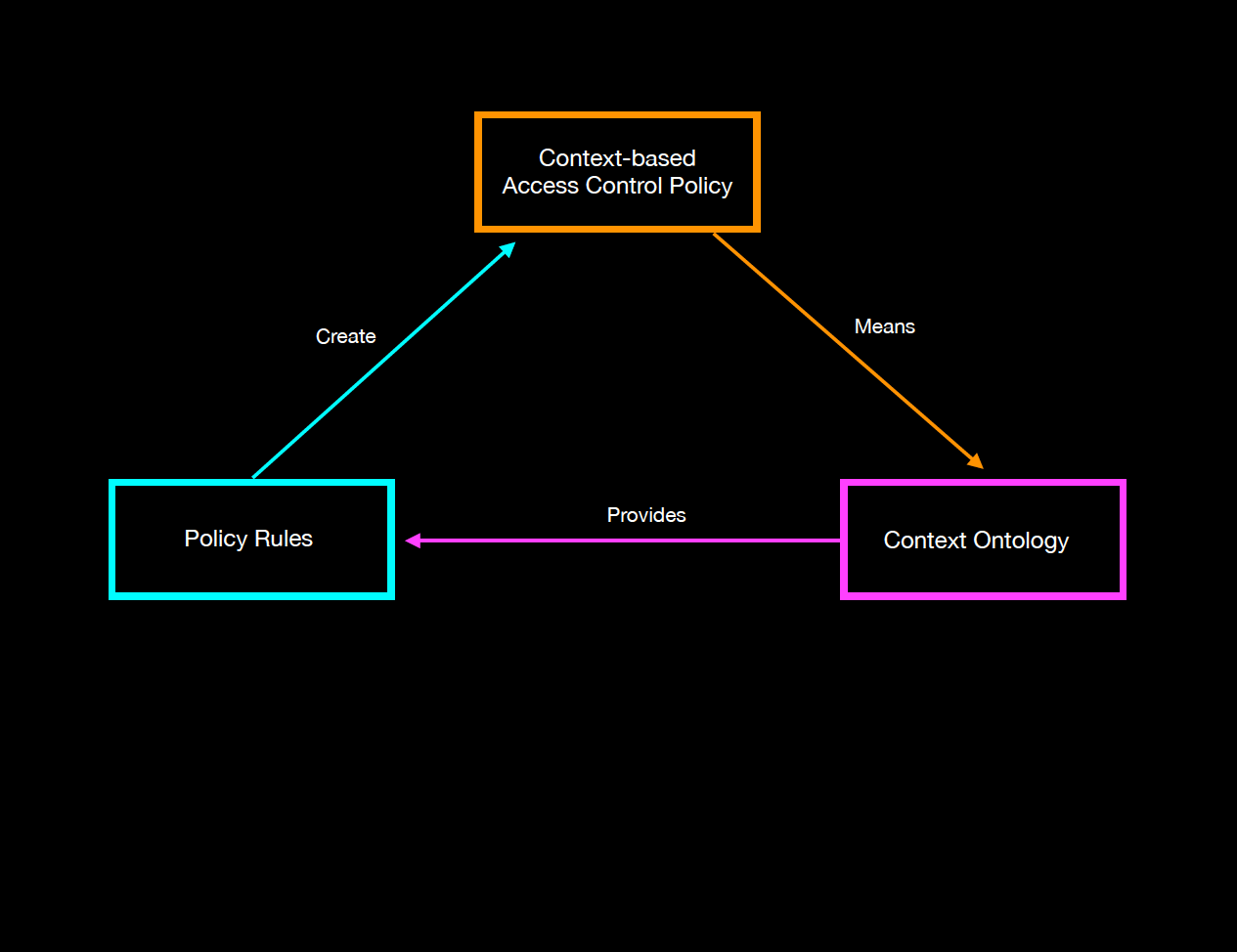
Context-Based Access Control
Context-Based Access Control (CBAC) is a security mechanism that determines access permissions based on the context in which access requests are made. Unlike Attribute-Based Access Control (ABAC), which evaluates a wide array of attributes, CBAC focuses on situational factors such as the user's location, the time of access, the sequence of prior actions, and the access history. This approach allows for dynamic adjustments to access permissions, enhancing security by considering real-time conditions.
For example, if users access Amazon.com from India, they are redirected to Amazon.in, providing a localized shopping experience. Similarly, a company might implement CBAC to restrict access to sensitive resources outside of business hours, mitigating the risk of unauthorized access during off-hours. In another example, a user's access might be granted or denied based on the sequence of steps they have previously taken in the system, ensuring that they follow the correct workflow. By leveraging contextual information, CBAC can provide more adaptive and responsive security measures tailored to the specific circumstances of each access attempt. This not only enhances security but also empowers the organization with the ability to control access in a more nuanced and effective manner.
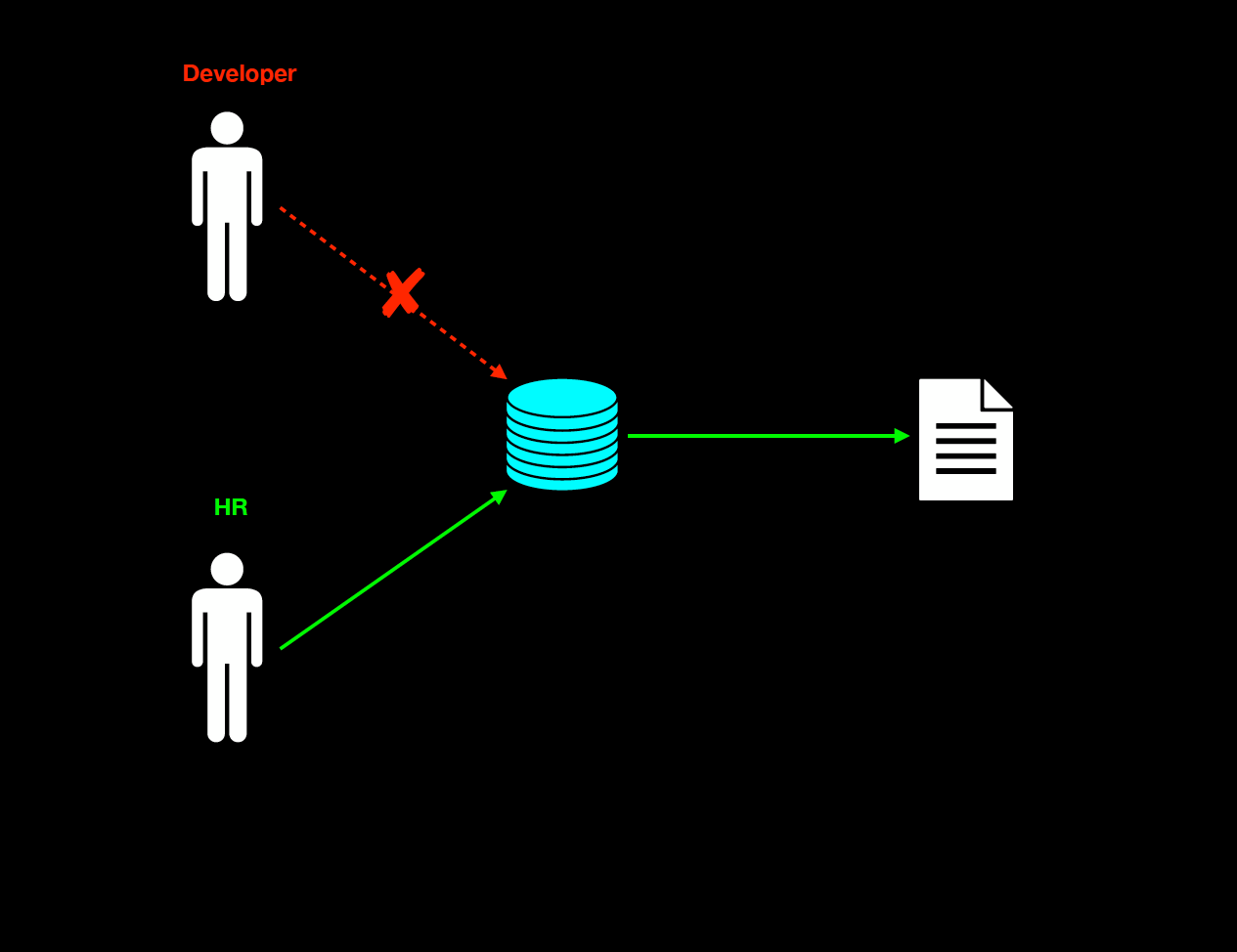
Content-Based Access Control
Content-Based Access Control (CBAC) regulates access based on the attributes or content of the accessed data. This approach is beneficial when access needs to be finely tuned to specific information within a larger dataset. For example, within a payroll system, a manager may have access to the payroll database but is restricted to viewing records only of their direct reports, ensuring the confidentiality of other employees' salary information.
In a document management system, access can be controlled at a granular level, allowing users to view or edit only certain parts of a document based on its content. For instance, general employees might have access to read a policy document, but only HR personnel can view sections containing sensitive employee data. As another example, doctors might have full access to a patient's medical history in a healthcare system. At the same time, administrative staff can only see non-medical information such as patient contact details. Specific medical data, like mental health records, might only be accessible to authorized mental health professionals. This level of control is achieved by analyzing the content of the data and applying rules that dictate who can access what information. Content-Based Access Control enhances security by ensuring users interact only with data relevant to their role and authorization level, thus protecting sensitive information from unauthorized access.
Accountability
Accountability in information security is the ability to trace actions within a system back to the responsible party. This involves maintaining comprehensive audit logs that record who acted, what action was taken when it occurred, and what resources were involved. These logs are crucial for detecting security incidents, conducting audits, ensuring regulatory compliance, and maintaining system integrity. In other words, accountability ensures that every action within a system can be attributed to a specific user, application, or process, making it easier to identify and address any security issues that may arise.
Non-repudiation, a critical accountability component, ensures that individuals cannot deny their actions. This is often achieved through digital signatures, secure logging, and other cryptographic methods that provide irrefutable evidence of user activities. In simpler terms, non-repudiation means that once a user has acted within a system, they cannot later deny doing so. This is important for maintaining the system's integrity and ensuring all actions can be reviewed and verified.
For example, in a financial system, accountability mechanisms ensure that every transaction can be traced back to the user who initiated it. This traceability is essential for internal controls and external audits, helping to detect and prevent fraudulent activities. Accountability measures uphold information systems' security, reliability, and trustworthiness by maintaining detailed and tamper-proof logs, ensuring that all actions can be reviewed and verified.


