Defense in Depth
Let's explore the intricate Defense in Depth strategy. Imagine a futuristic fortress with a tower at its core, protecting a valuable resource or crown jewel. This fortress is fortified with multiple secure walls, meticulously arranged in concentric circles around the building. Each wall features a distinct security control, such as a biometric scanner, a firewall, or a security guard. These mechanisms are intricately designed to deter unauthorized intruders from reaching the crown jewel. Beyond preventing unauthorized access, the fortress has physical controls like reinforced doors or fire suppression systems to mitigate damage or loss from physical attacks or natural disasters. This analogy highlights the complexity and synergy of multiple security layers, each with unique security controls, working together to protect data, the crown jewel.
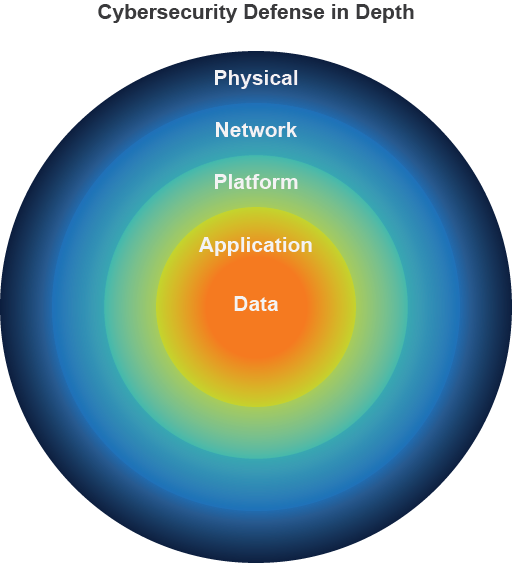
Physical Security
As the first layer within the Defense in Depth strategy, the physical layer is pivotal in preventing intruders from accessing, compromising, or destroying the physical infrastructure containing the crown jewel—data. While cyber-attacks are often directed at the logical layers, attacks on critical infrastructure, such as data centers, are rare. This rarity underscores the effectiveness and reliability of the physical layer in the Defense in Depth strategy. Examples of physical controls that help protect critical infrastructure are walls, CCTV cameras, RFID-locked doors, biometric and motion scanners, security guards, guard dogs, fire suppression systems, HVAC systems, and reinforced fences.
Network Security
The second layer within the concept of Defense in Depth is the network layer. A primary way to secure a network is through network traffic monitoring and analysis, and firewalls are one of the controls that help monitor network traffic, preventing unauthorized access. Additionally, firewalls can allow or block network traffic dictated by security or policy rules. Another set of controls within this layer are Intrusion detection systems (IDS) and Intrusion prevention systems (IPS), which work synergistically with infrastructure networks and endpoint firewalls as they help identify threats and respond accordingly. Other network controls include microsegmentation, endpoint security, VPN, and Zero Trust Architecture (ZTA), a security model that requires strict identity verification for every person and device trying to access resources on a network, regardless of whether they are inside or outside the network perimeter. This is exemplified by Google's BeyondCorp initiative, which redefines network security through continuous verification, a process that ensures the ongoing validity of a user's identity and device security posture, strict access controls, and comprehensive monitoring regarding network security.
Platform Security
As the third layer within the Defense in Depth strategy, Platform Security focuses on the security architecture and its inherent tools and processes that work synergistically to secure various underlying systems that are the foundation on which applications and services run. These systems include endpoints, servers, virtual machines (VM), operating systems, firmware, and containers. System security controls in this layer refer to the tools and processes implemented to secure these underlying systems. Some examples of system security controls in this layer include the following:
- Host-based Intrusion Detection Systems (HIDS) and Host-based Intrusion Prevention Systems (HIPS): HIDS monitors a single host for suspicious activity and potential threats. At the same time, HIPS can actively block or prevent detected threats on the host.
- Host-based Firewalls are software firewalls installed on individual hosts that control incoming and outgoing network traffic based on security rules, protecting the host from unauthorized access.
- Endpoint Anti-Malware Software refers to programs installed on endpoints to detect, prevent, and remove malicious software. These programs protect endpoint devices from malware, a typical cyber threat.
- Server System Hardening through Ports and Services Restrictions: Configuring servers to turn off unnecessary ports and services, adhering to security configuration baselines to reduce the attack surface.
- Automated Patch Management: Using automated tools to regularly update software and systems with the latest security patches to protect against vulnerabilities.
- Access Controls such as Role-Based Access Controls (RBAC) and Multi-Factor Authentication (MFA): RBAC assigns permissions based on user roles. MFA requires multiple forms of verification for access, enhancing security.
- Log Monitoring: Continuously reviewing logs from systems and applications to detect and respond to suspicious activities or security incidents.
- Using VMs to Isolate Applications, Services, and Processes: Running different applications in separate VMs to prevent a compromise or failure in one VM from affecting others, enhancing security and stability.
- Ensuring Container Security Using Minimal Base Images and Scanning for Vulnerabilities: Create container images with only essential components (i.e., base OS, application code, dependencies, configuration files, runtime environments, etc.) and regularly scan them for vulnerabilities to reduce the attack surface and ensure a secure container environment.
Application Security
The Application Security layer involves developing, adding, and testing application security features to prevent vulnerabilities like unauthorized access and alteration. Application security also involves measures taken during application development and deployment to avoid threats such as data or code within an application being stolen or hijacked. Application Security controls include IDE security, which refers to the security measures implemented within the Integrated Development Environment (IDE) to ensure the code's security. Other controls include static code analysis, software composition analysis (SCA), dynamic application security testing, and API security.
- Secure Coding Practices: Adherence to secure coding standards to prevent vulnerabilities like SQL injection, XSS, etc.
- Application Penetration Testing: Regular testing of applications to find vulnerabilities.
- Authentication and Authorization: Mechanisms like OAuth multifactor authentication ensure users are who they say they are and have appropriate access.
- Static Code Analysis: The process of examining source code for vulnerabilities and coding errors without executing the program. This process helps identify potential security issues early in the development cycle.
- Static Application Security Testing (SAST): A subset of Static Code Analysis, this process focuses more on the application's security, meaning it identifies vulnerabilities that can be exploited be attackers. Some of the security vulnerabilities that SAST seeks to root out are SQL injection, cross-site scripting (XSS), buffer overflows, and similar potential security flaws.
- Software Composition Analysis (SCA): The practice of identifying and managing open-source components or dependencies within software to ensure security and compliance with licensing requirements. It also helps detect known vulnerabilities in third-party libraries.
- Dynamic Application Security Testing (DAST): A method of testing the running application to identify vulnerabilities by simulating attacks. It focuses on the application's operational state to find security flaws that may not be evident in the source code.
- API Security: The practice of securing Application Programming Interfaces (APIs) by implementing measures such as authentication, authorization, input validation, and rate limiting to protect against threats and ensure secure data exchange between applications.
Data Security
The Data Security Layer is not just a part of the Defense in Depth strategy, but its heart and soul. Within this layer lies the crown jewel that the layers above aim to shield and protect through various intricate controls. The crown jewel is the data. This layer is not just a safeguard but a fortress at the center, protecting data from unauthorized access and alterations, regardless of location or transmission method. Various controls at this core layer include encryption, access controls, and data loss prevention, and the weight of our responsibility to ensure this invaluable resource's security. I've concisely described some controls at this layer below:
- Data Encryption protects data by converting it into a coded format that can only be read by someone with the correct decryption key, ensuring the confidentiality of data both at rest (stored data) and in transit (data being transmitted).
- Data Masking: This procedure obfuscates specific data within a database to protect sensitive information, showing fictitious data instead of actual data during non-production scenarios, such as testing and development.
- Access Controls: Implement policies like Role-Based Access Control (RBAC) to ensure only authorized users can access specific data. Limiting data access based on user roles and permissions minimizes the risk of data breaches.
- Data Loss Prevention (DLP): Monitors and controls data transfer to prevent unauthorized sharing, leakage, or loss of sensitive data. DLP solutions can block or alert risky data movements.
- Tokenization: This process replaces sensitive data elements with non-sensitive equivalents (tokens) with no exploitable value outside a specific context. It is often used in payment processing to protect credit card information.
- Data Classification: This process assigns categories to data based on its sensitivity and criticality to the organization, which helps apply appropriate security controls and handling practices based on the classification level.
- Immutable Storage: Ensures that once data is written, it cannot be modified or deleted. This is often used for logs and backup data to protect against tampering and unauthorized changes.
- Database Activity Monitoring (DAM) continuously monitors and analyzes database activities to detect and respond to unauthorized or suspicious actions, which helps identify potential breaches and enforce security policies.
- Backup and Recovery: Regularly creates copies of data and stores them securely to ensure data can be recovered in case of accidental loss, corruption, or ransomware attacks, ensuring data availability and integrity.
- Auditing and Logging: Maintain detailed records of data access and modification activities. This helps track data usage, detect anomalies, and ensure compliance with regulatory requirements.
- Secure Deletion: This method ensures that when data is no longer needed, it is completely and securely erased, making it unrecoverable. This prevents unauthorized access to sensitive data that is no longer in use.
- Data Anonymization removes or alters personally identifiable information (PII) from data sets so individuals cannot be identified. This is crucial for complying with privacy regulations and protecting user privacy during data analysis.
By implementing these controls, organizations can strengthen their data security layer, protecting sensitive information from unauthorized access, breaches, and data loss. Implementing a robust defense-in-depth strategy involves effectively integrating these layers to provide a holistic security posture that significantly mitigates risks. Each layer builds upon the last, creating a comprehensive shield against security threats. It's essential to note that not all cyberattacks target data. Some cyberattacks deny data availability through various means, such as overwhelming network and computing resources through DDoS (Distributed Denial of Service) attacks that use botnet endpoints orchestrated by command and control servers to generate overwhelming traffic, taking down data availability. When data availability is compromised, it affects the availability component of the CIA triad. For details about the CIA triad, please check out my article that explains each component.

