Security Groups

This resource shows how cloud firewalls work. In AWS, you can customize an EC2 instance's firewall to meet an organization's security requirements.
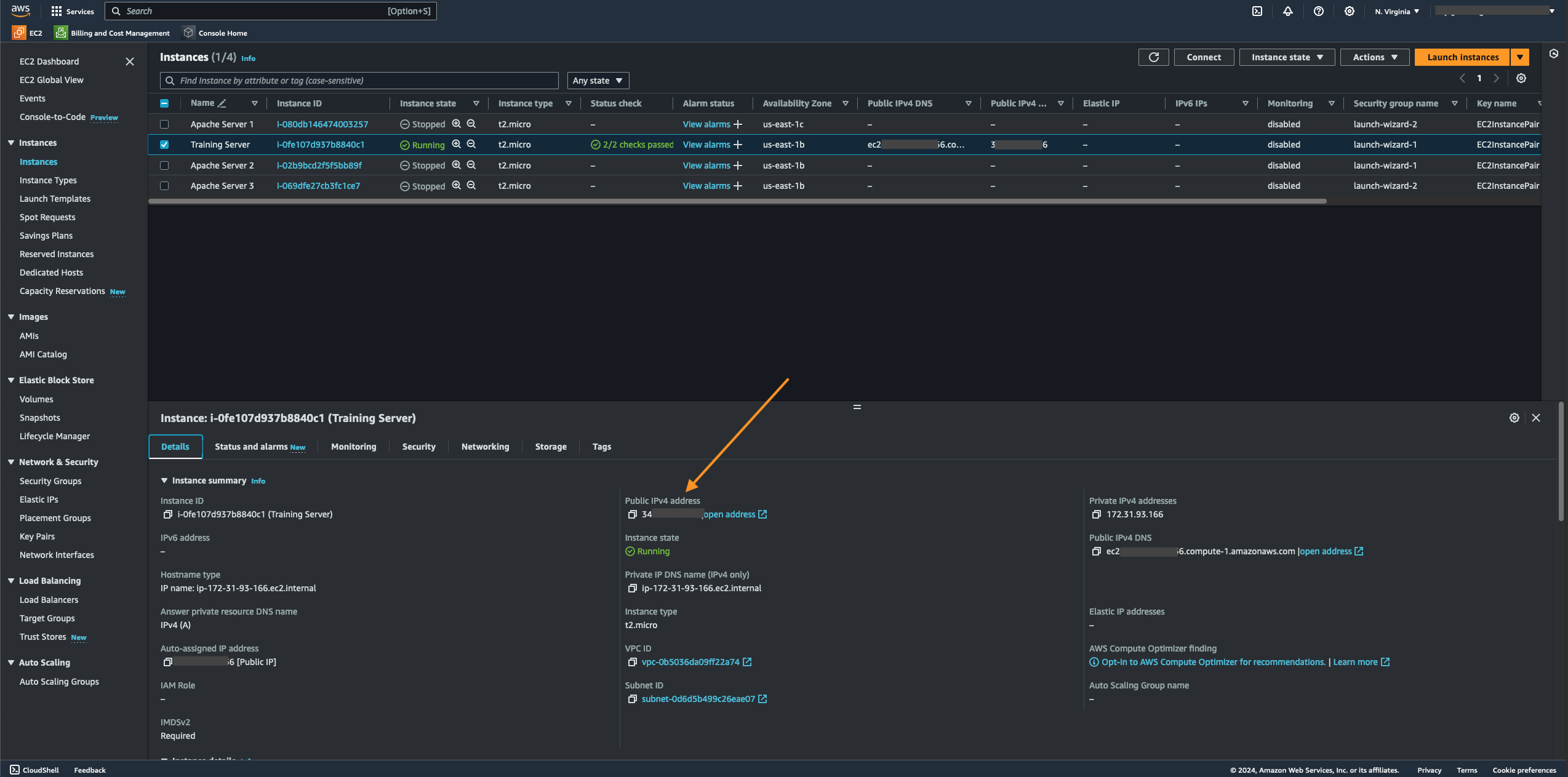
- Launch an existing EC2 instance by navigating to Instance State, then select Start Instance.
- Once the selected EC2 instance runs, you can access its public IP to verify that the server works. You can access the instance's public IP under the Details tab.
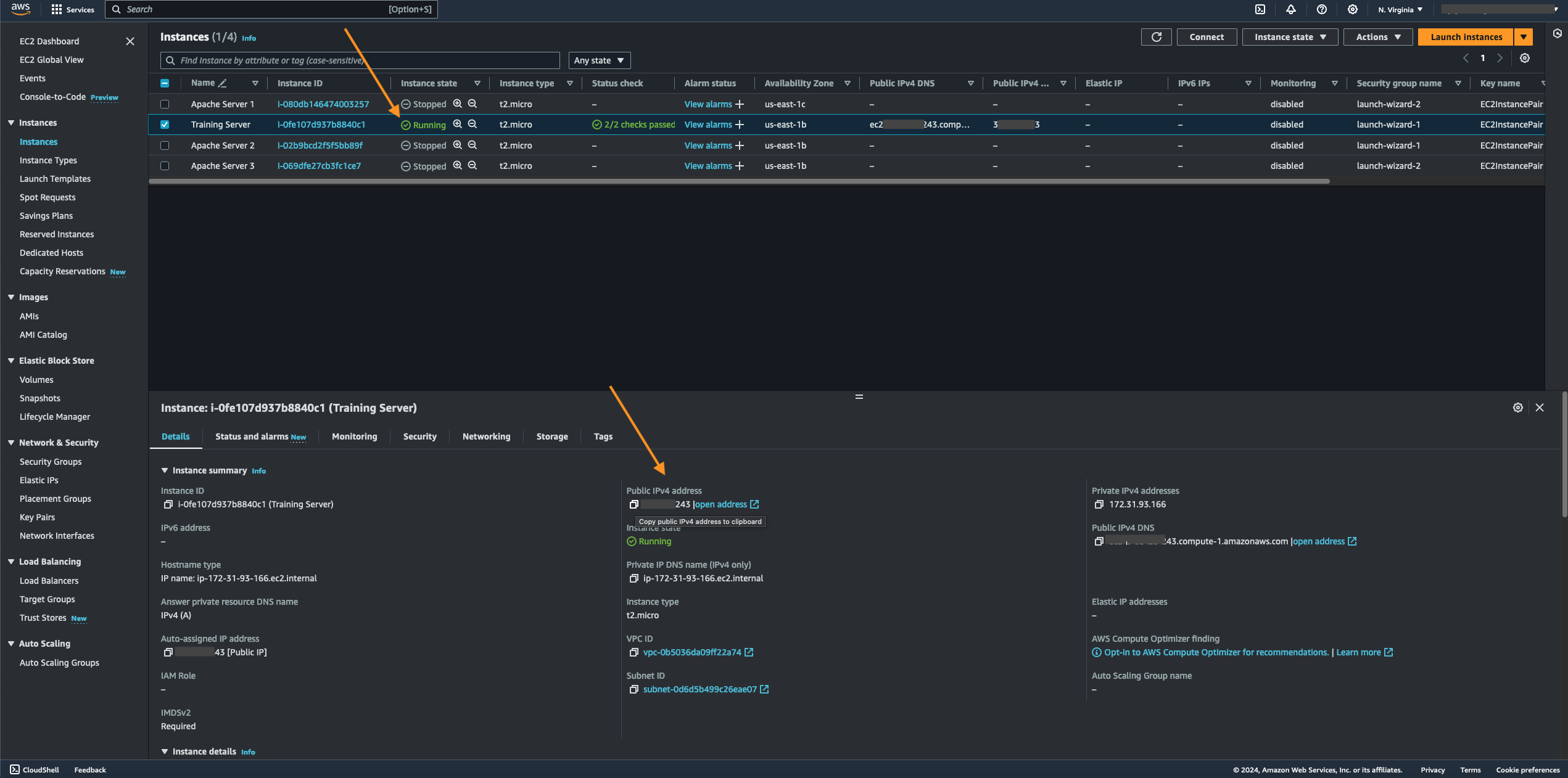
- If the EC2 instance was configured with a script under its user data, its output will be displayed on a browser page. You can refer to my "Creating an EC2 Instance" article for the steps in configuring a script for the instance's user data. As you can see, the way this particular instance's inbound rules are configured makes it publicly accessible to any sources through the Internet, which is not secure and is a serious security issue.

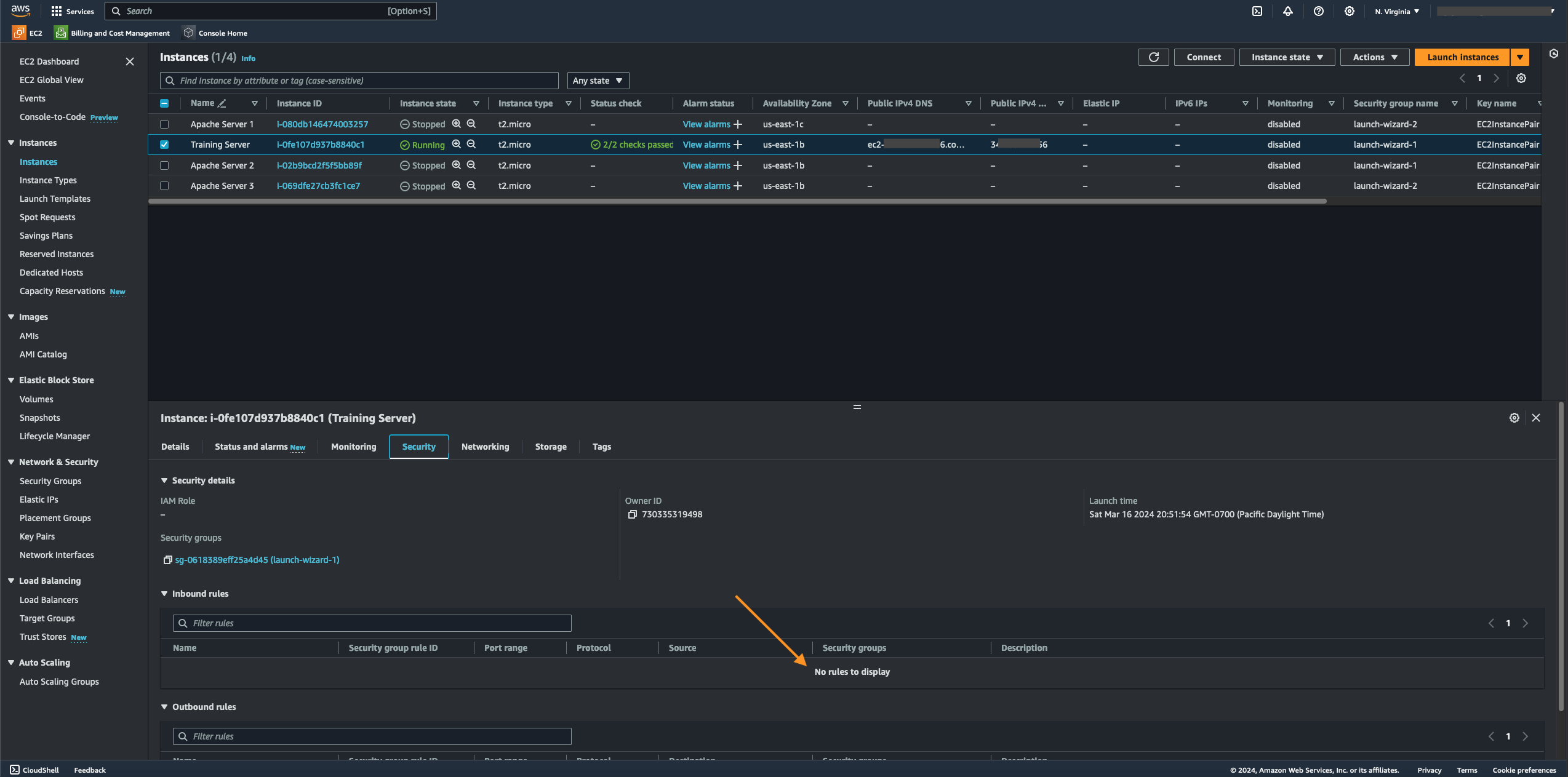
- Selecting the "Security" tab lets you ascertain the various inbound and outbound rules under a specific security group assigned to the EC2 instance. In this case, you can see that the server allows for any IP source, which is indicated by an IP address and subnet of 0.0.0.0/0 under the "Source" tab, to access the server on port 80, as it is configured under the instance's "Port Range" tab. To reconfigure the selected instance's inbound rules, select its specific security group by clicking the "Security groups" link under the Security tab.
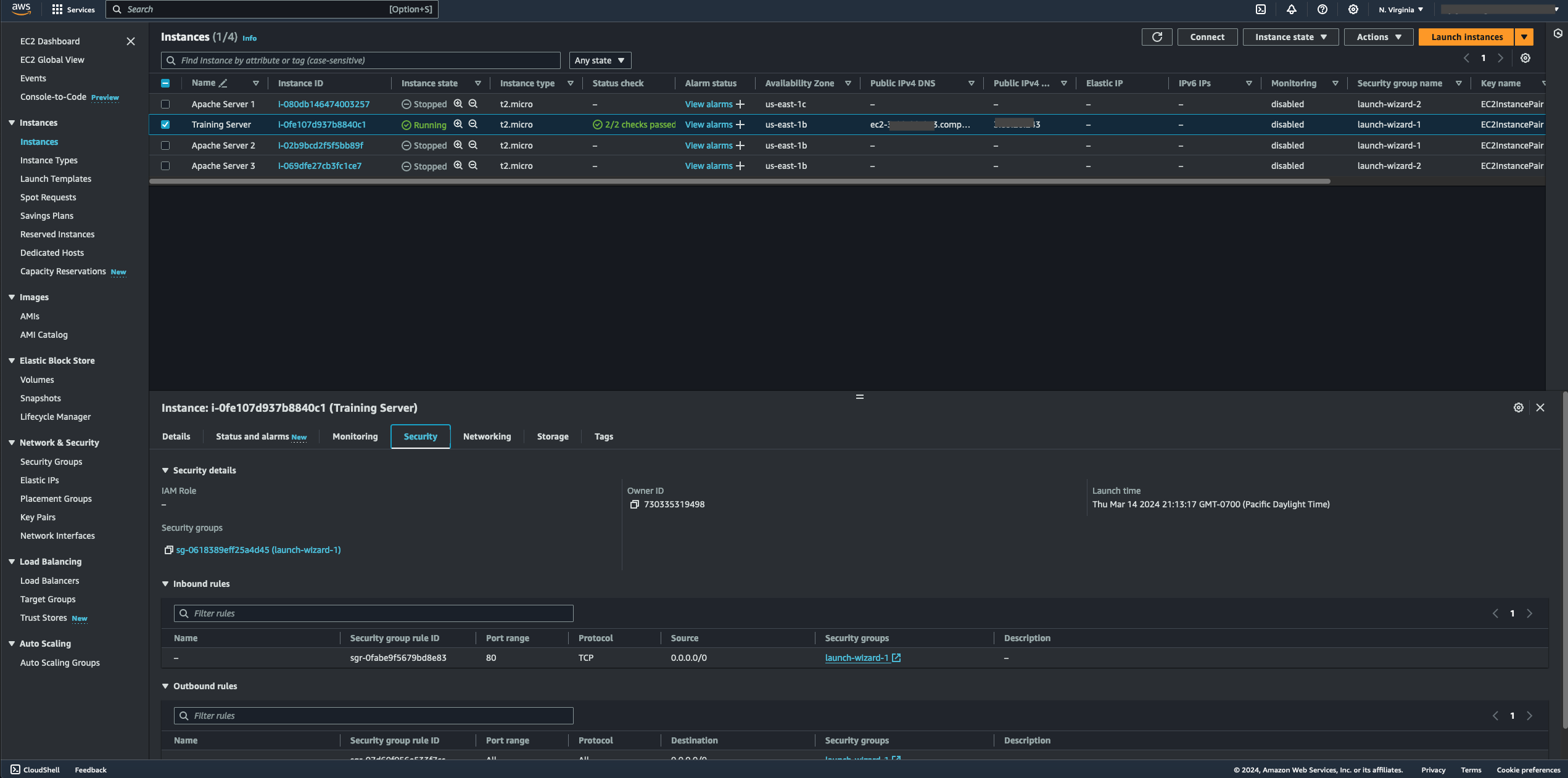
- After selecting the instance's security group, navigate to the "Inbound rules" tab to view how the server's inbound rules are configured. You can see that any IP address and subnet source, signified by how 0.0.0.0/0 was configured under "Source," can access the instance from the internet, which is unsecured and prone to attacks.
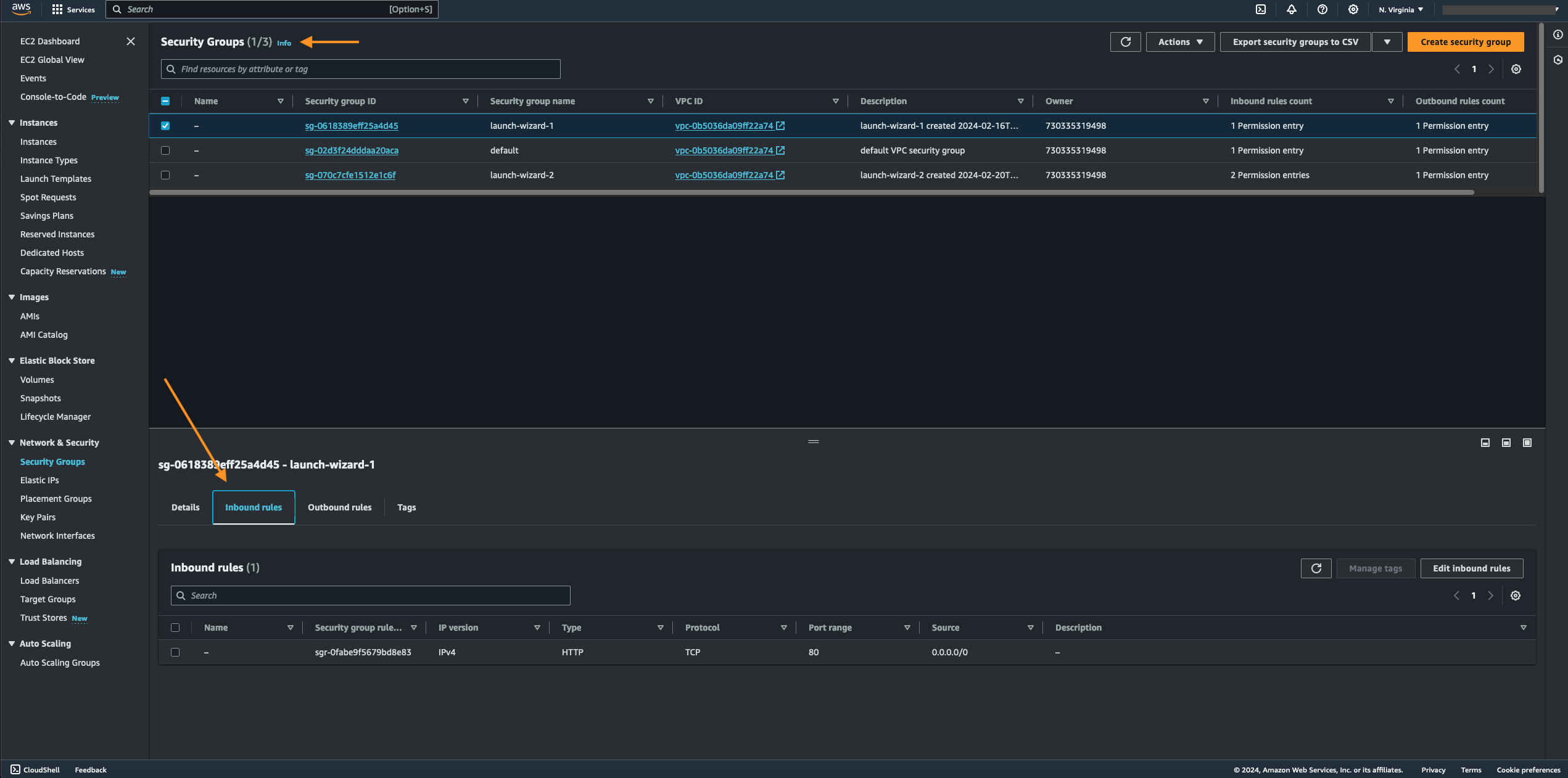
- You can address an instance's unsecured inbound rules by selecting "Edit inbound rules," either by selecting "Actions" from the drop-down menu on the upper right-hand side of the selected security group or by selecting the "Inbound Rules" tab and clicking on the "Edit Inbound Rules" button located on the lower right-hand side that corresponds to the security group that needs to be reconfigured.
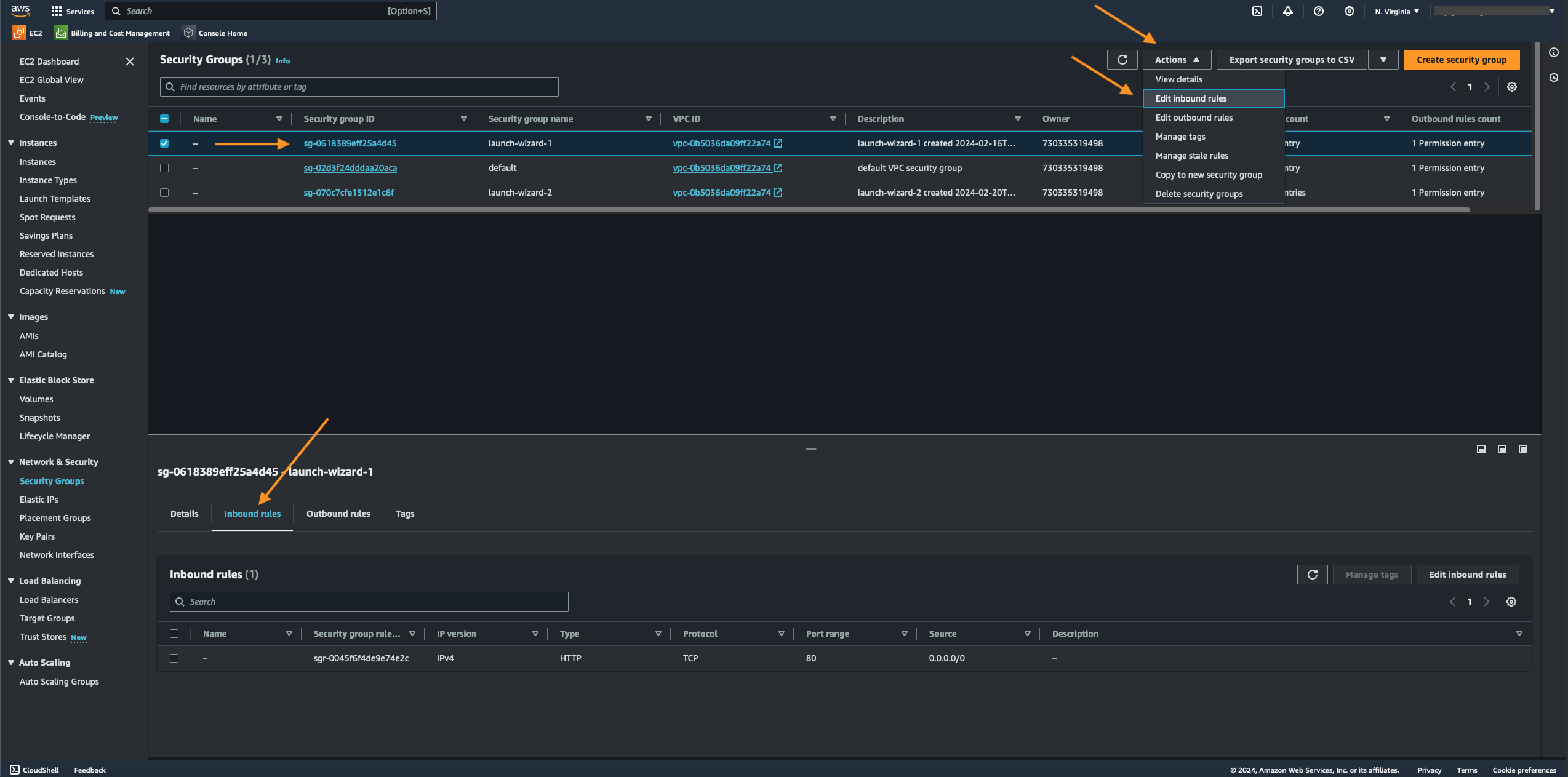
- Since the current EC2 instance's inbound rules are unsecured, we will delete it, removing the configured 0.0.0.0/0 IP source. An EC2 instance's inbound rules configuration functions similarly to a hardware network firewall; however, unlike a hardware network firewall, it's based in the cloud, which is impressive.
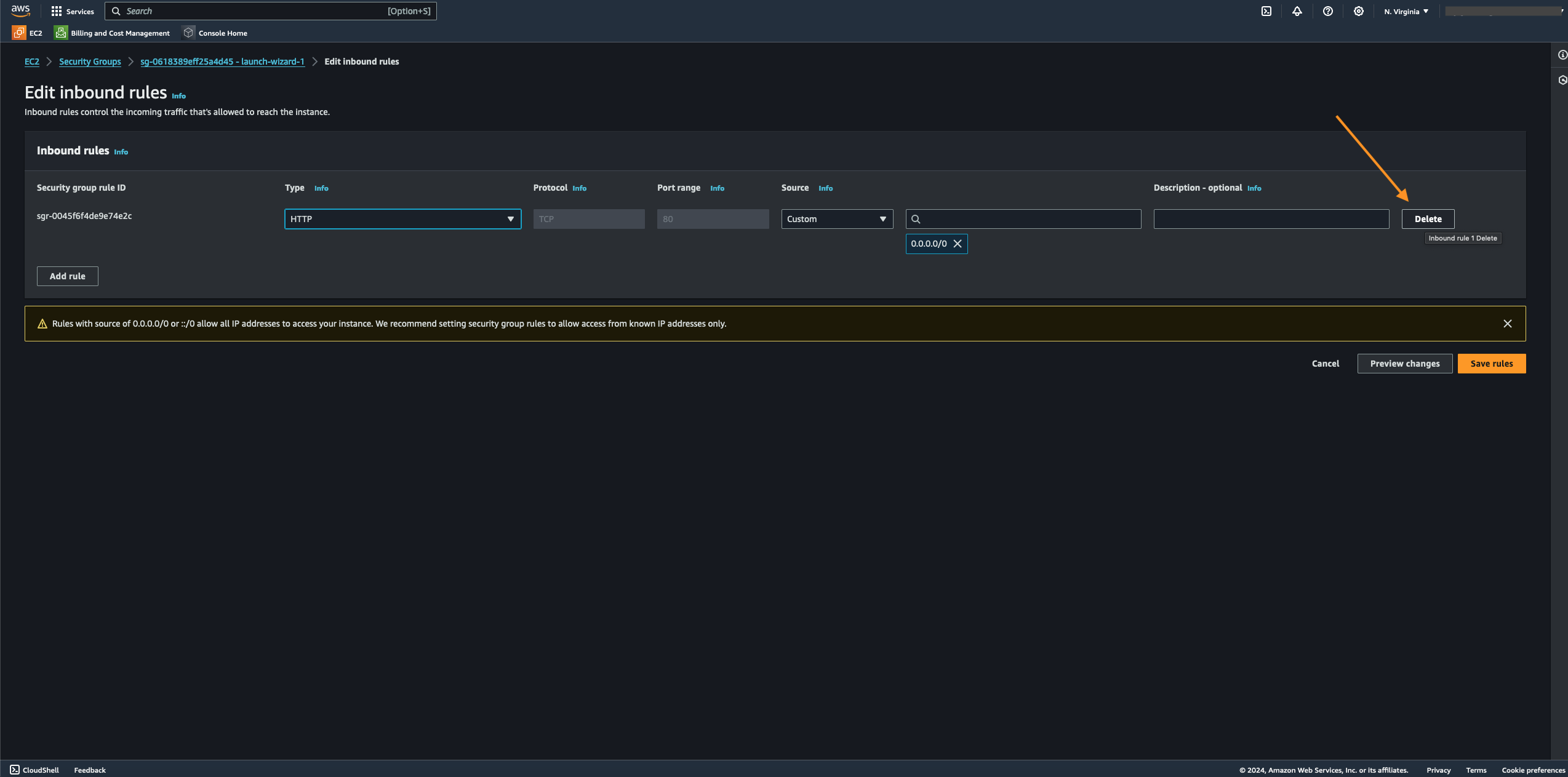
- We just removed the instance's unsecured inbound rule, which blocks anyone from accessing it over the public internet. To implement the change in the inbound rules, click the "Save" button. Although we made the instance more secure, we also made it unavailable to the public, which is not cool. We need to make sure that we balance security and convenience. So, let's not stop here and keep working on it. Now that we've deleted the instance's unsecured inbound rule, access to the instance is prevented over the public internet. While we've secured the instance, we also prevented access from the public internet, making the third aspect of the CIA triad, "Availability," non-existent. This is not where we should stop since cybersecurity must balance security and convenience.
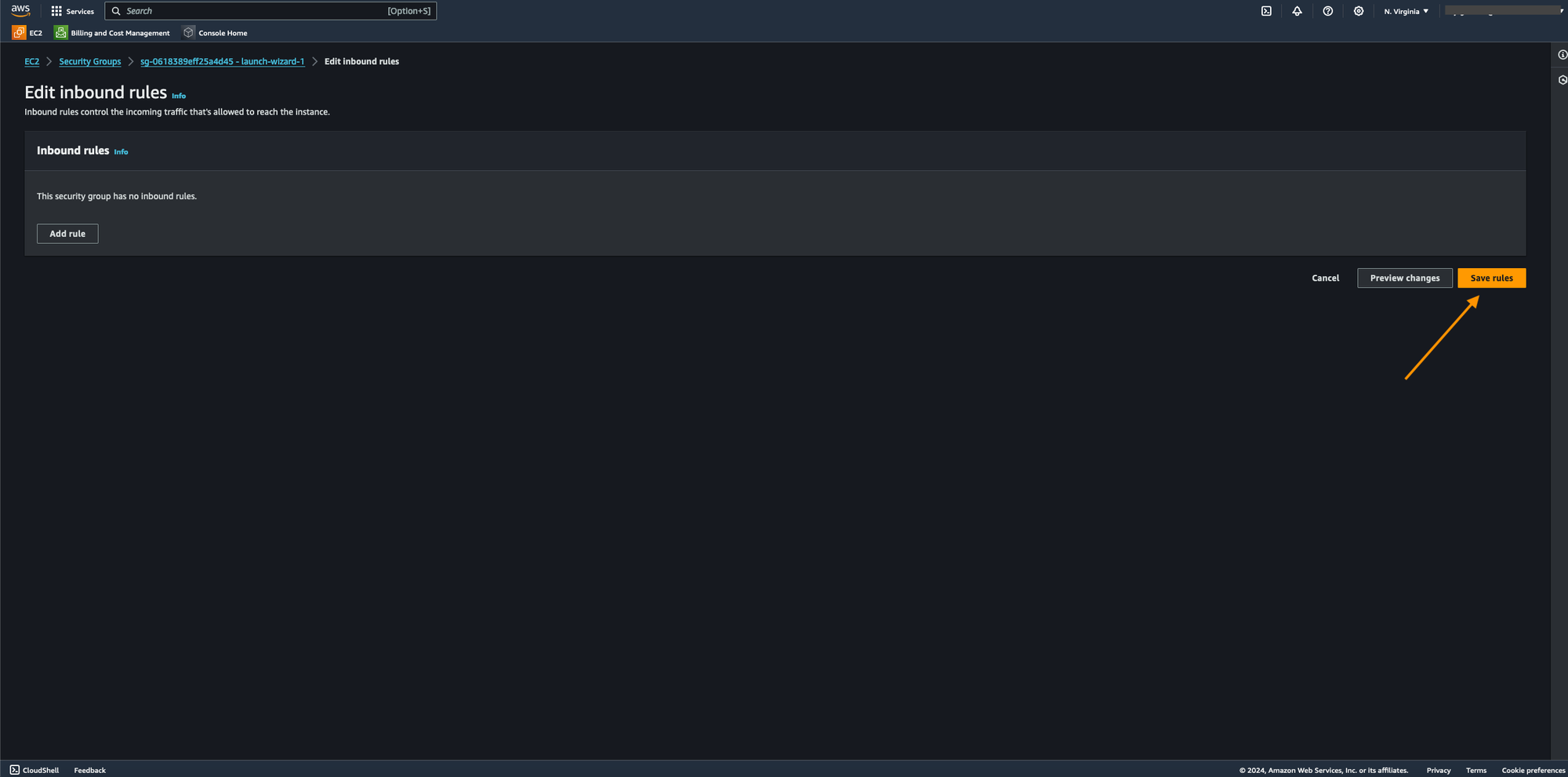
- As we can see, there are no rules under the instance's Inbound rules.
- To verify that we indeed cannot access the EC2 instance using its public IP address, we copy and paste its public IP into a browser's address bar. Now, you can see that the cloud server fails to load, confirming that we no longer have access to it.