Creating an Application Load Balancer

An Application Load Balancer (ALB) is a powerful tool that evenly distributes incoming traffic across multiple EC2 instances, preventing any one instance from becoming overwhelmed. This not only improves the application's availability and uptime but also enhances its security and scalability, making it a key component in addressing the availability aspect of the CIA triad.
Application Load Balancers can also automatically adjust traffic distribution based on the application's load, allowing it to scale horizontally as computing demand fluctuates. Additionally, ALBs can reroute traffic to healthy instances if one or more EC2 instances fail, ensuring fault tolerance and continuous normal operations through redundant virtual servers. By balancing the load across multiple instances, ALBs can improve application performance by reducing response time and preventing overload on any single instance, thereby enhancing performance, reliability, and scalability.
ALBs play a crucial role in enhancing security by reducing the attack surface and number of entry points. They achieve this by centralizing access, integrating with security services, offloading SSL/TLS termination, and providing tight control over network access. A standout security feature is the ability to conduct health checks on specific groups of EC2 instances, ensuring that only healthy instances receive traffic. These features work together to minimize potential vulnerabilities and entry points that attackers can exploit, thereby significantly improving an application's overall security.
- I navigated to EC2/Instances and launched and configured a few instances, giving each one a name. From the available image options, I selected "Amazon Linux AWS" as my AMI for this demonstration. Under Architecture, I chose 64-bit (x86), and for the instance type, I selected t2.micro.
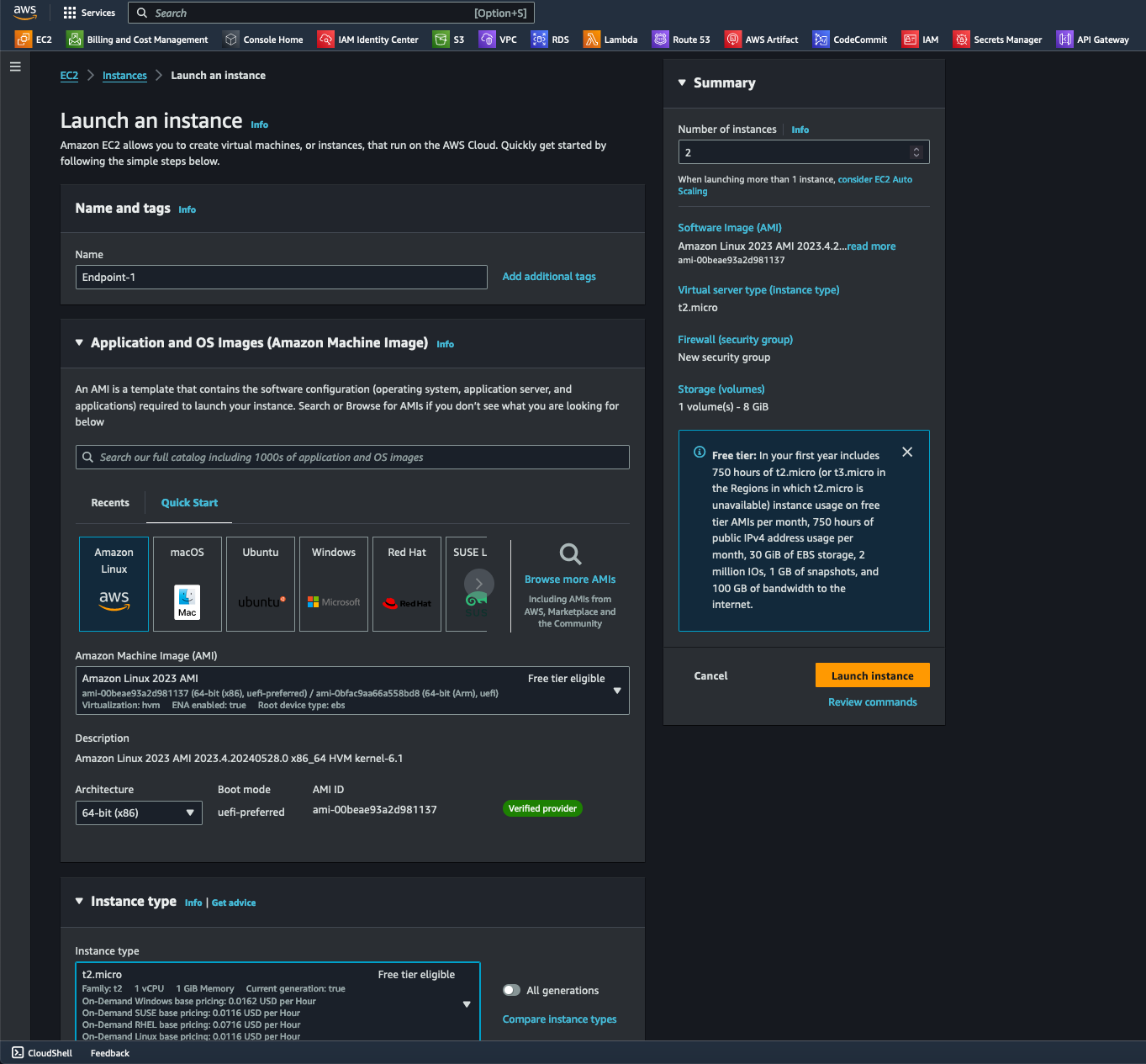
- While I don't recommend it for security purposes, I selected "Proceed without a key pair" under the Key pair (login) option for this time. A key pair allows secure SSH access to EC2 instances by authenticating users with the private key corresponding to the instance's public key.
- Using a test code block, I configured the User Data option. I then launched the instance before I could view all instances.
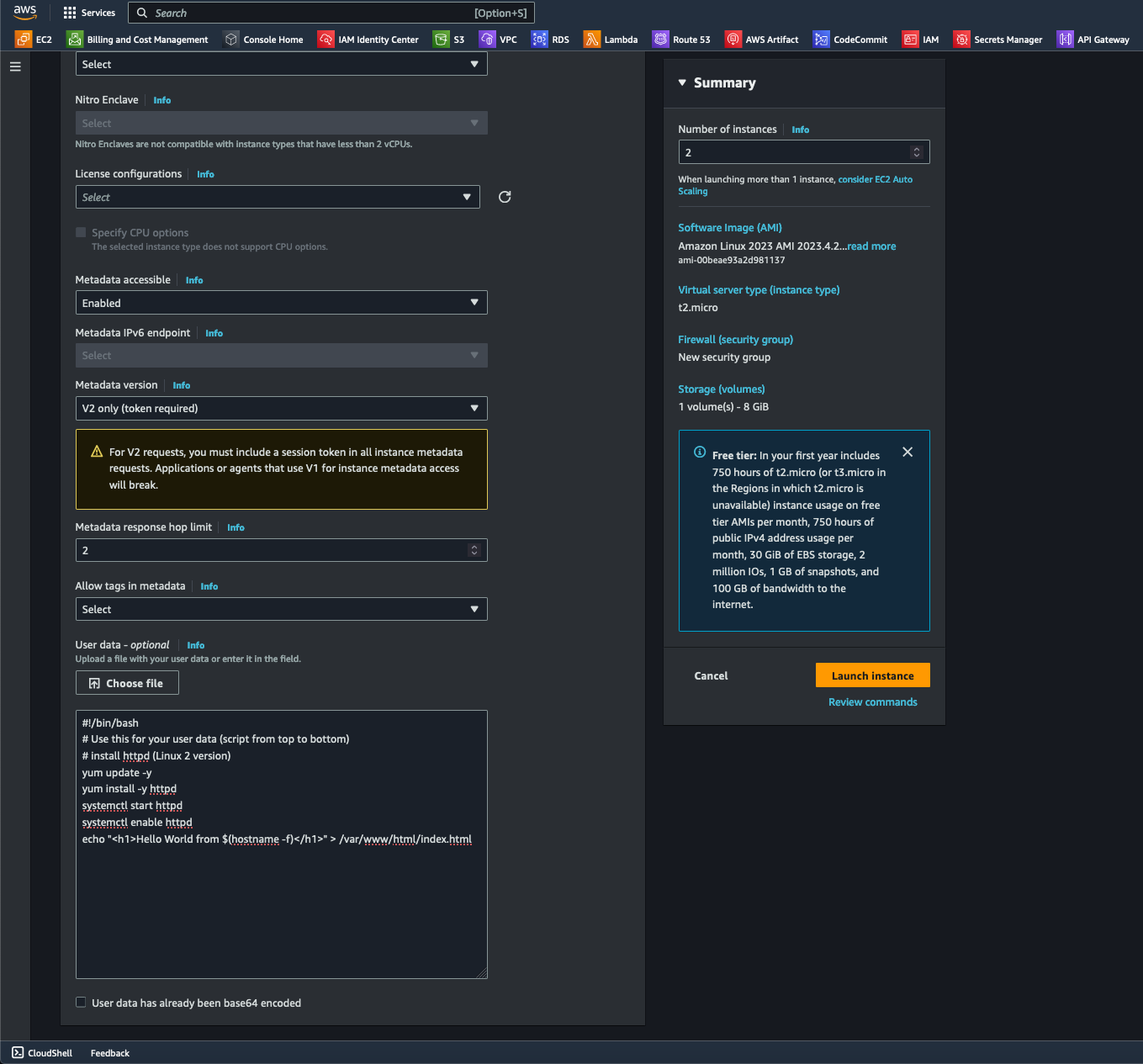
Code Block
# Use this for your user data (script from top to bottom)
# install httpd (Linux 2 version)
yum update -y
yum install -y httpd
systemctl start httpd
systemctl enable httpd
echo "<h1>Hello World from $(hostname -f)</h1>" > /var/www/html/index.html4. I renamed one of my endpoint instances to help distinguish each instance. Under the selected endpoint's details section, I copied its public IP address to test on a browser.
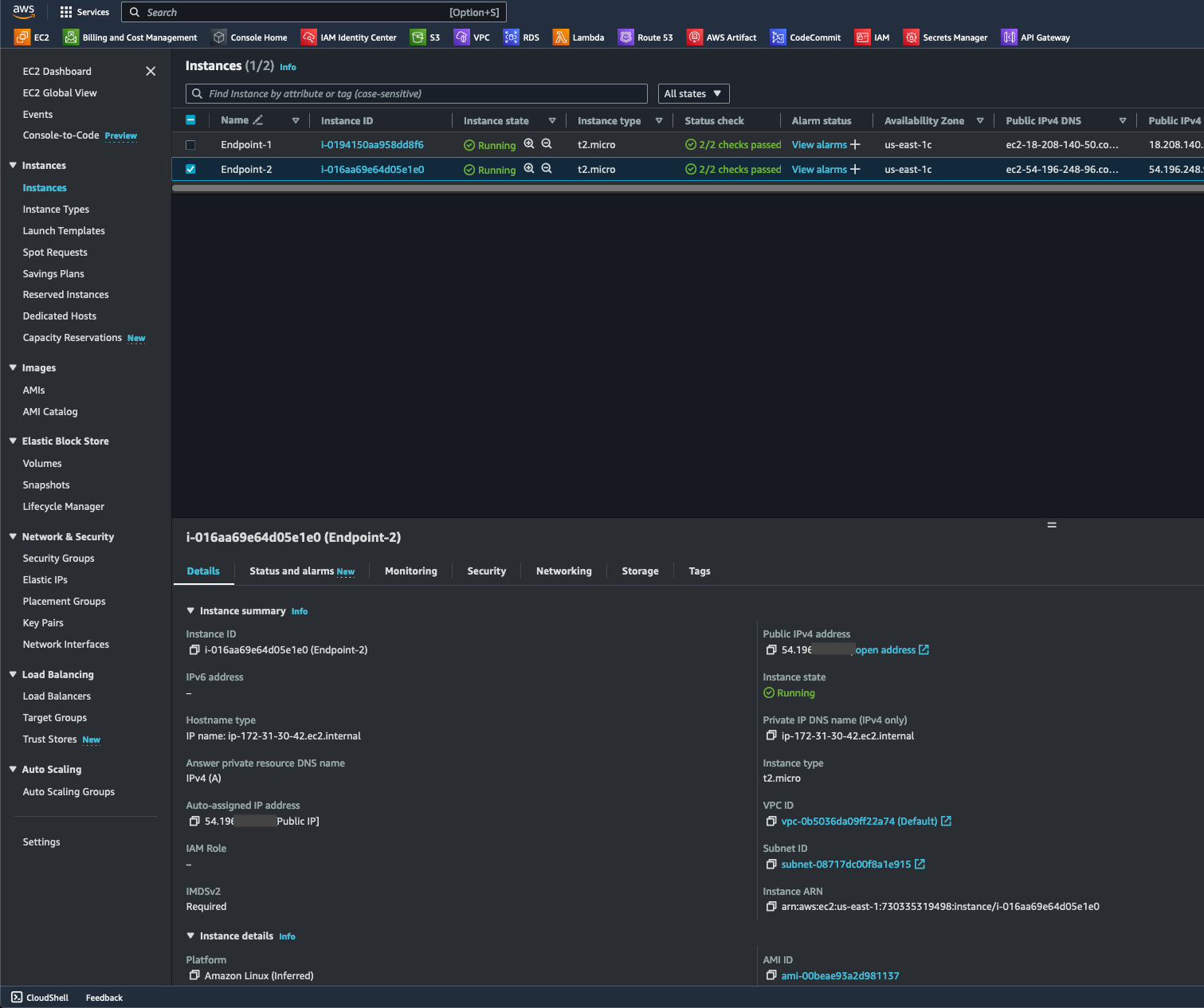
- After pasting the public IP address into a browser, Endpoint-2's user data is returned, as expected, signifying the instance's accessibility.

- I then navigated to the Load Balancers option before selecting "Create load balancer."
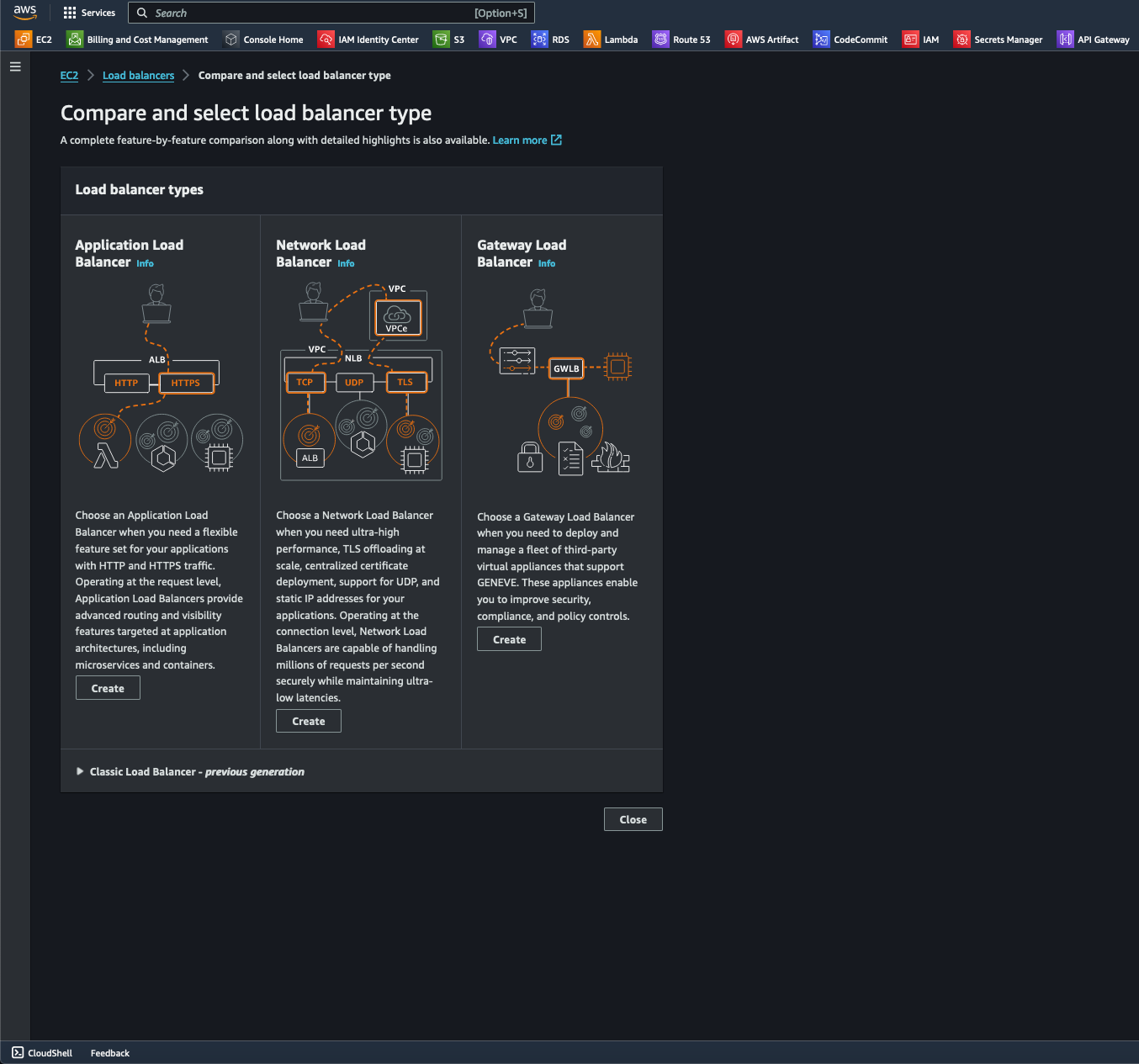
- Selecting the Application Load Balancer: The ALB allows clients to make requests to your application. The listeners in the load balancer receive requests based on the chosen protocol and port settings. The receiving listener checks the incoming request against the defined rules and, if necessary, directs the request to the appropriate target group. Using an HTTPS listener makes it possible to delegate the task of TLS encryption and decryption to a load balancer. Healthy targets in one or more target groups receive traffic according to the load-balancing algorithm and the routing rules specified by the listener.
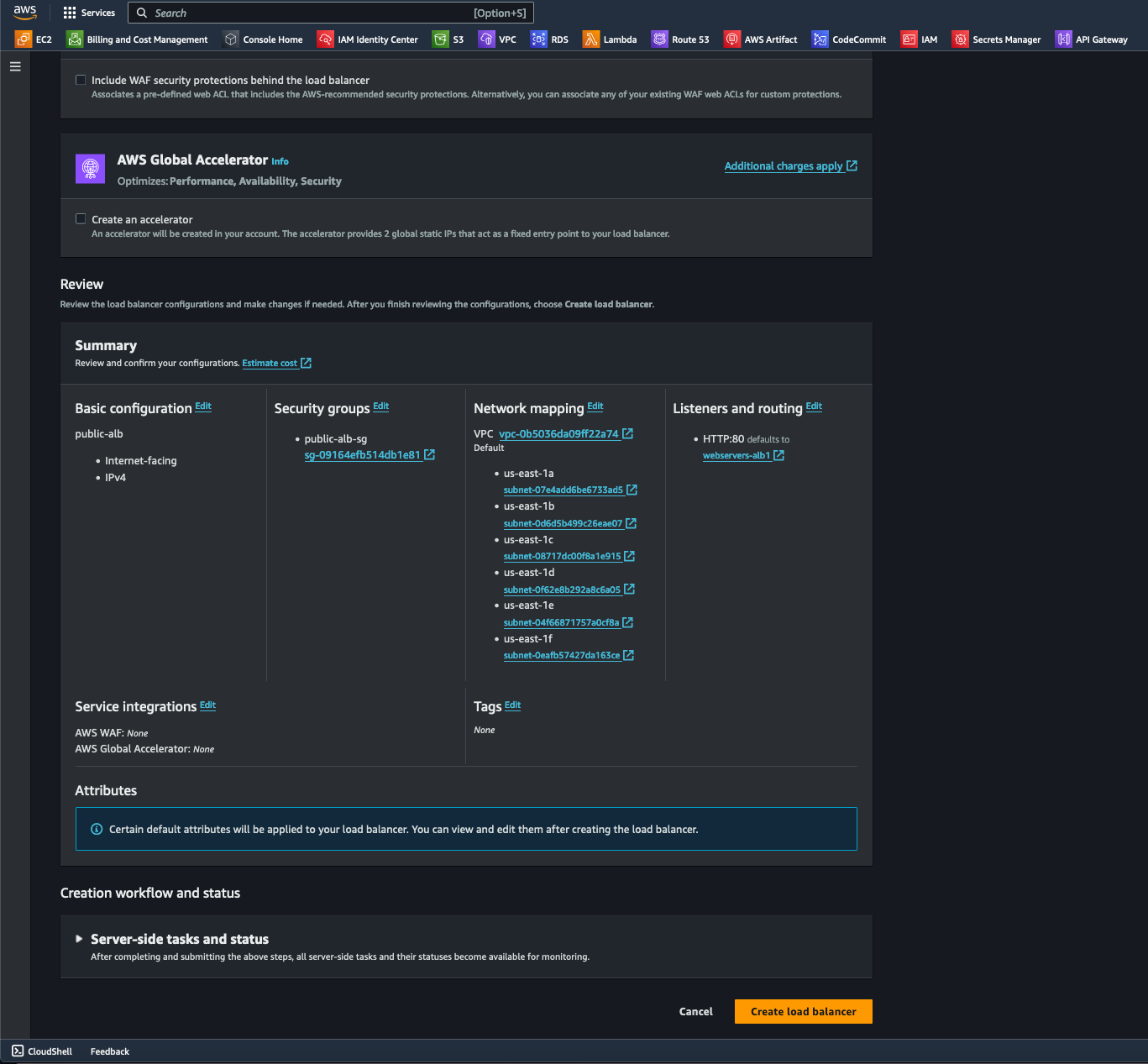
- Navigating to EC2/Load balancer, I configured the ALB's basic configurations by naming it, specifying Internet facing under the Scheme option, selecting IPv4-IP under the IP address type option, and choosing Default under VPC.
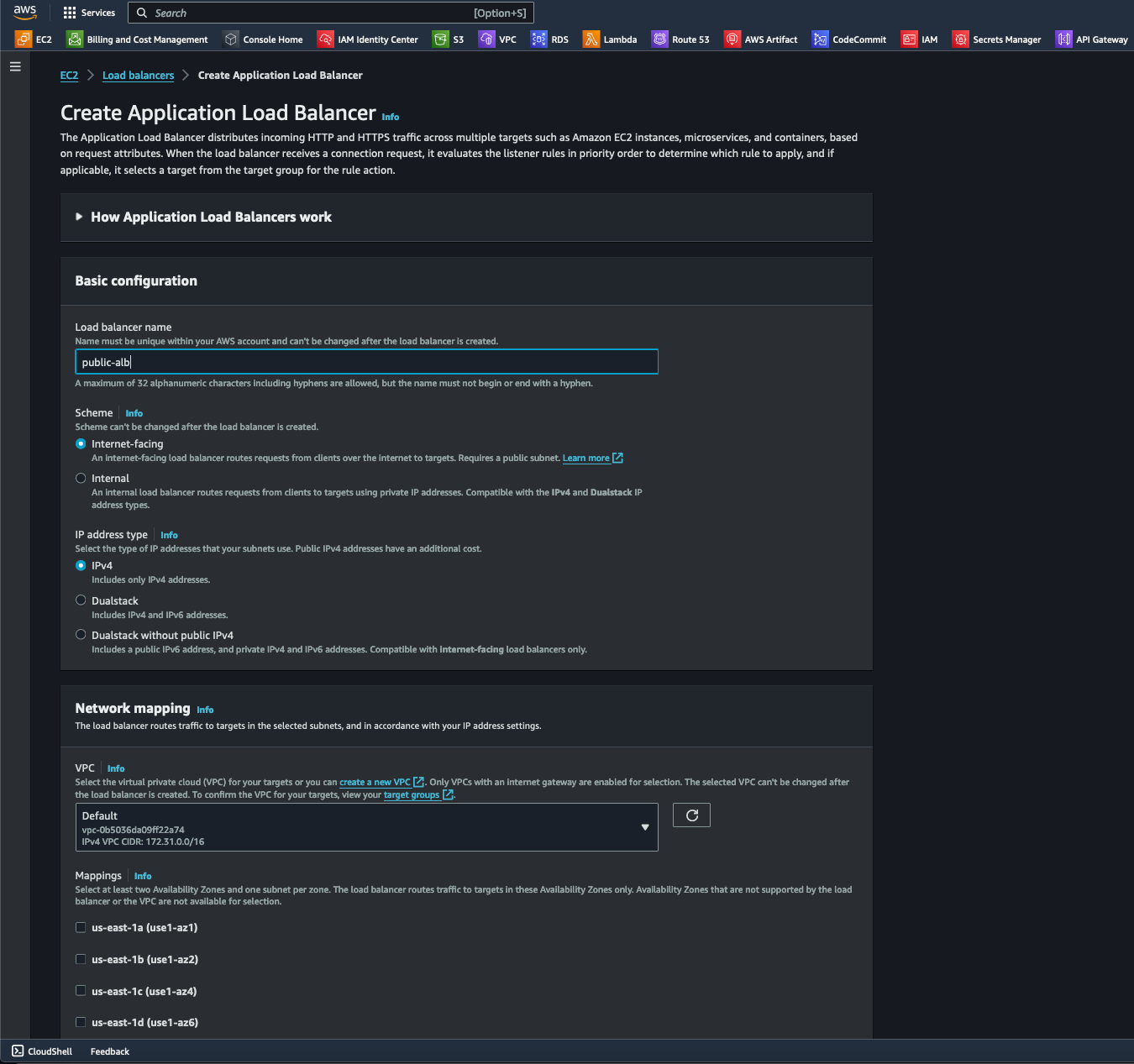
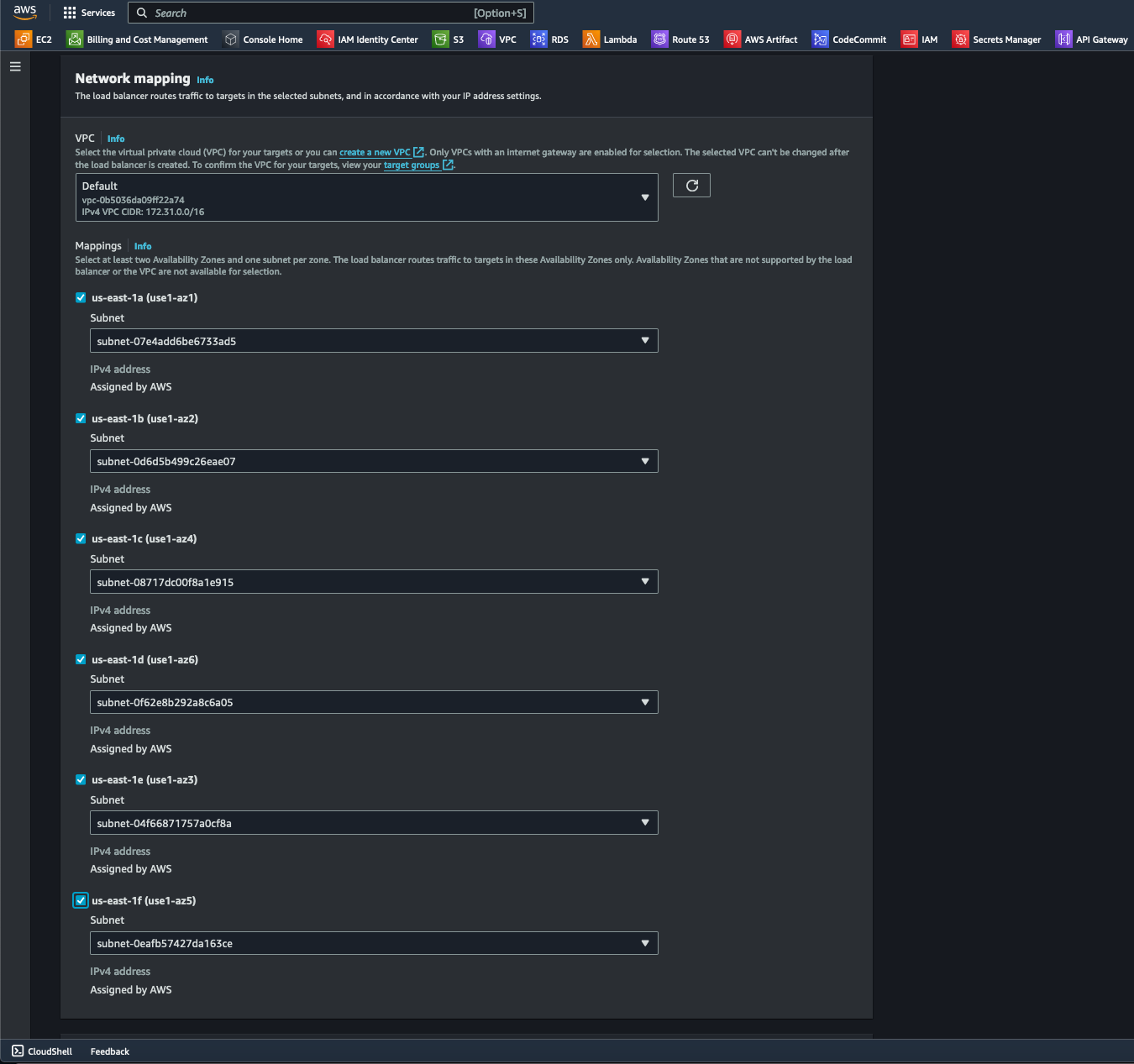
- Under the Network mapping section, I enabled all Availability Zones (AZ) to increase redundancy and fault tolerance.
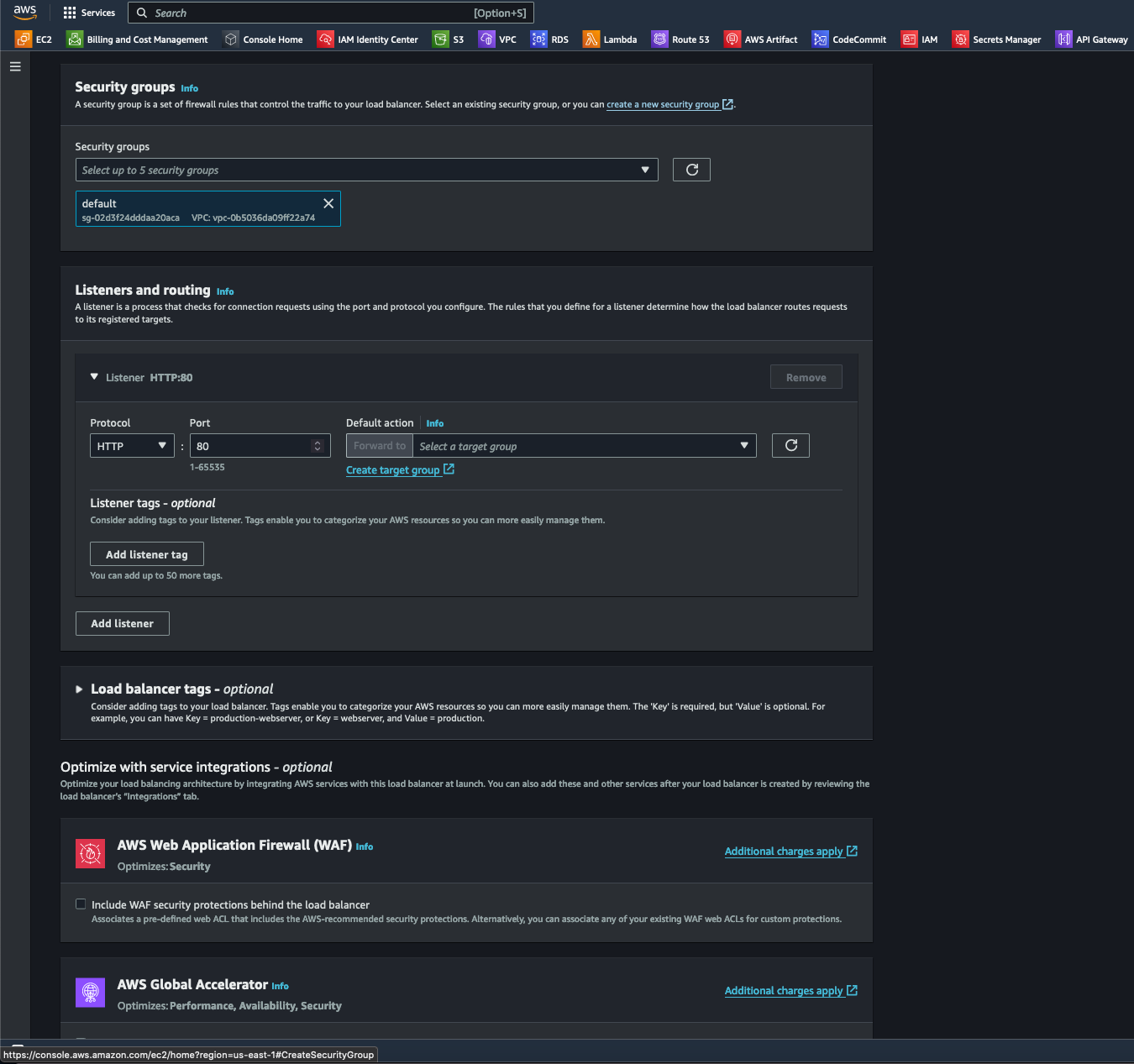
- For this step, I selected Create a new security group to configure the ALB's virtual firewall to manage inbound and outbound traffic at the network layer.
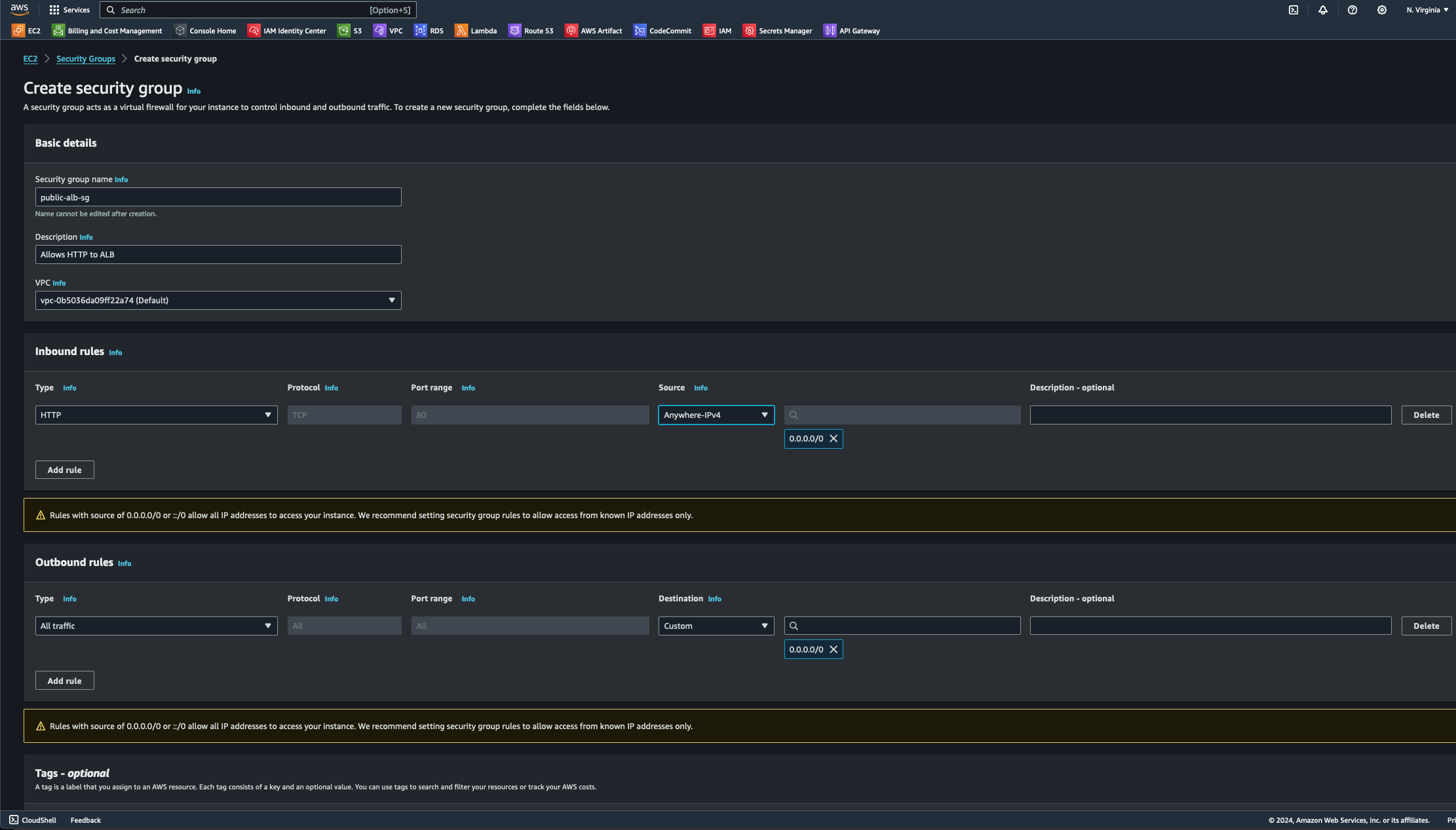
- Under EC2/Security Groups, I specified the inbound rules with the HTTP protocol and Anywhere IPv4 as the source. Since this ALB will be public-facing, configuring SSH under inbound rules is unnecessary. Once I verified the configurations, I selected the Create Security Group Button at the bottom right side of the page.
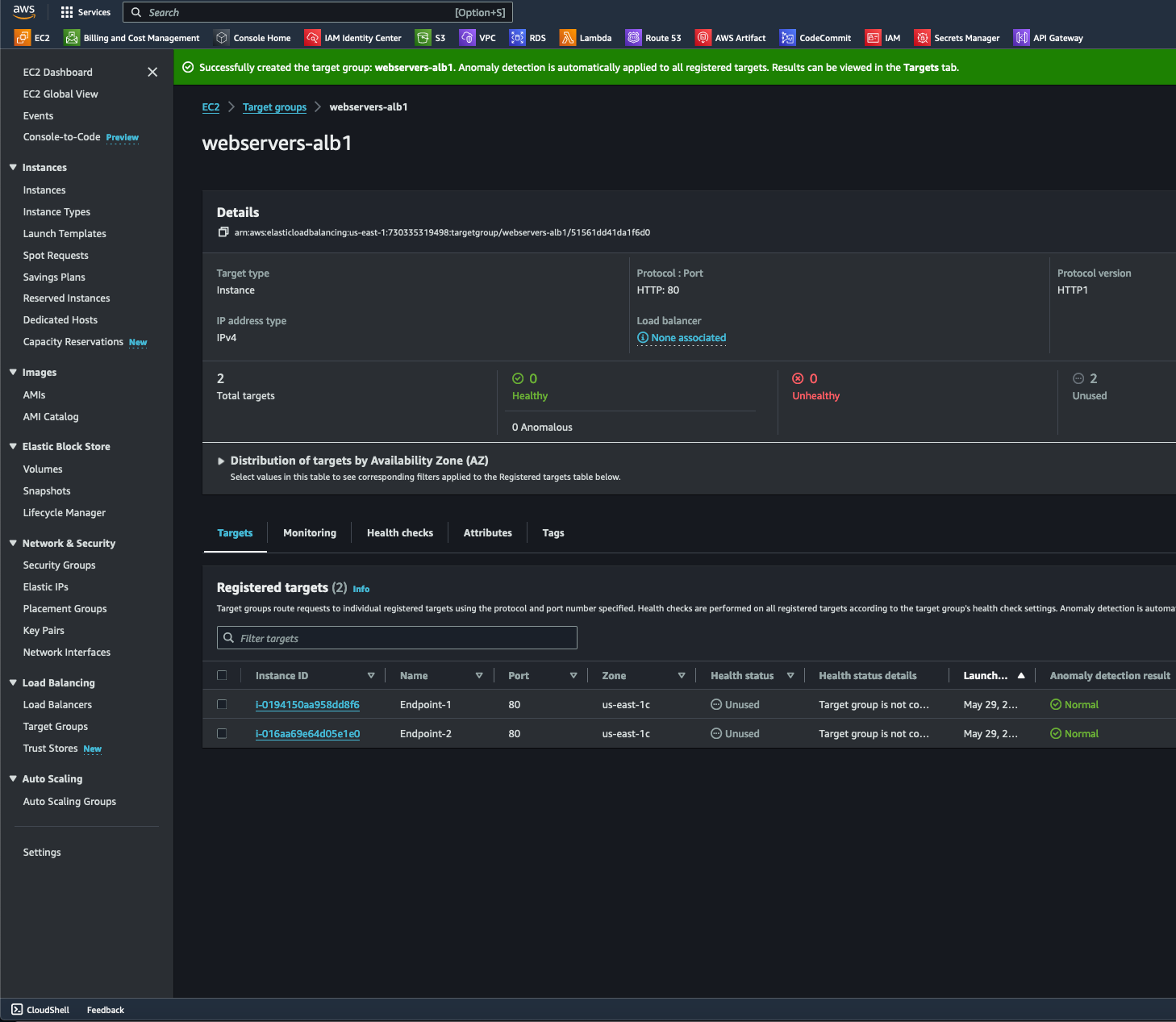
- After selecting the Created ALB option under the Listeners and Routing section, I selected Create Target Group. Specifying the target type, group name, transport protocol and port, and IP address type are some of the necessary configurations to get ALB to function.
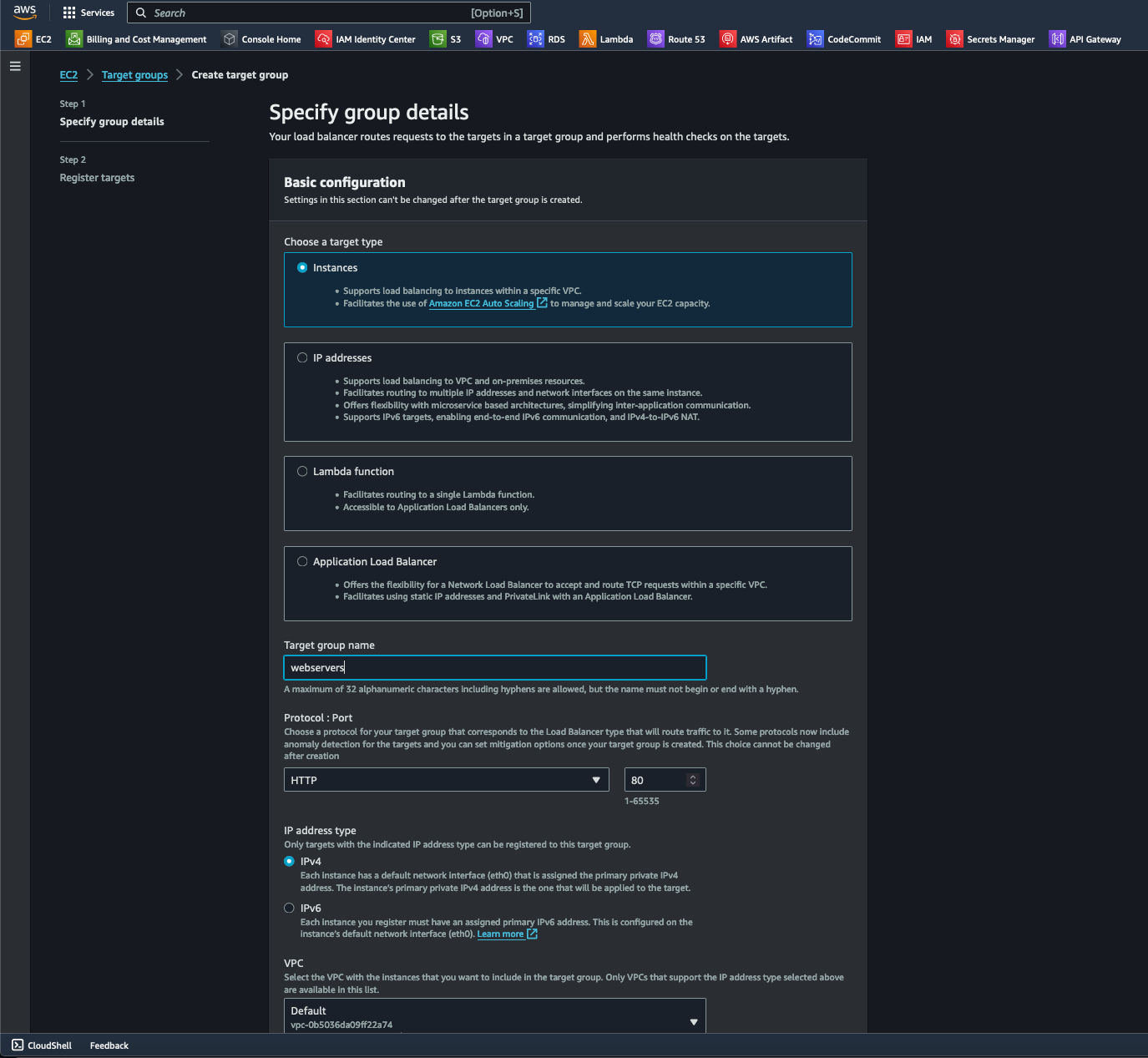
- Next, I then specified the VPC and protocol version. While HTTP2 and gRPC protocols are more advanced and efficient and can be used in more complex situations, I selected HTTP1 since it offers more compatibility with existing web infrastructure (including legacy systems) and applications. For Health checks, I configured "/" to perform health checks at the root before proceeding to the next step by selecting the Next button.
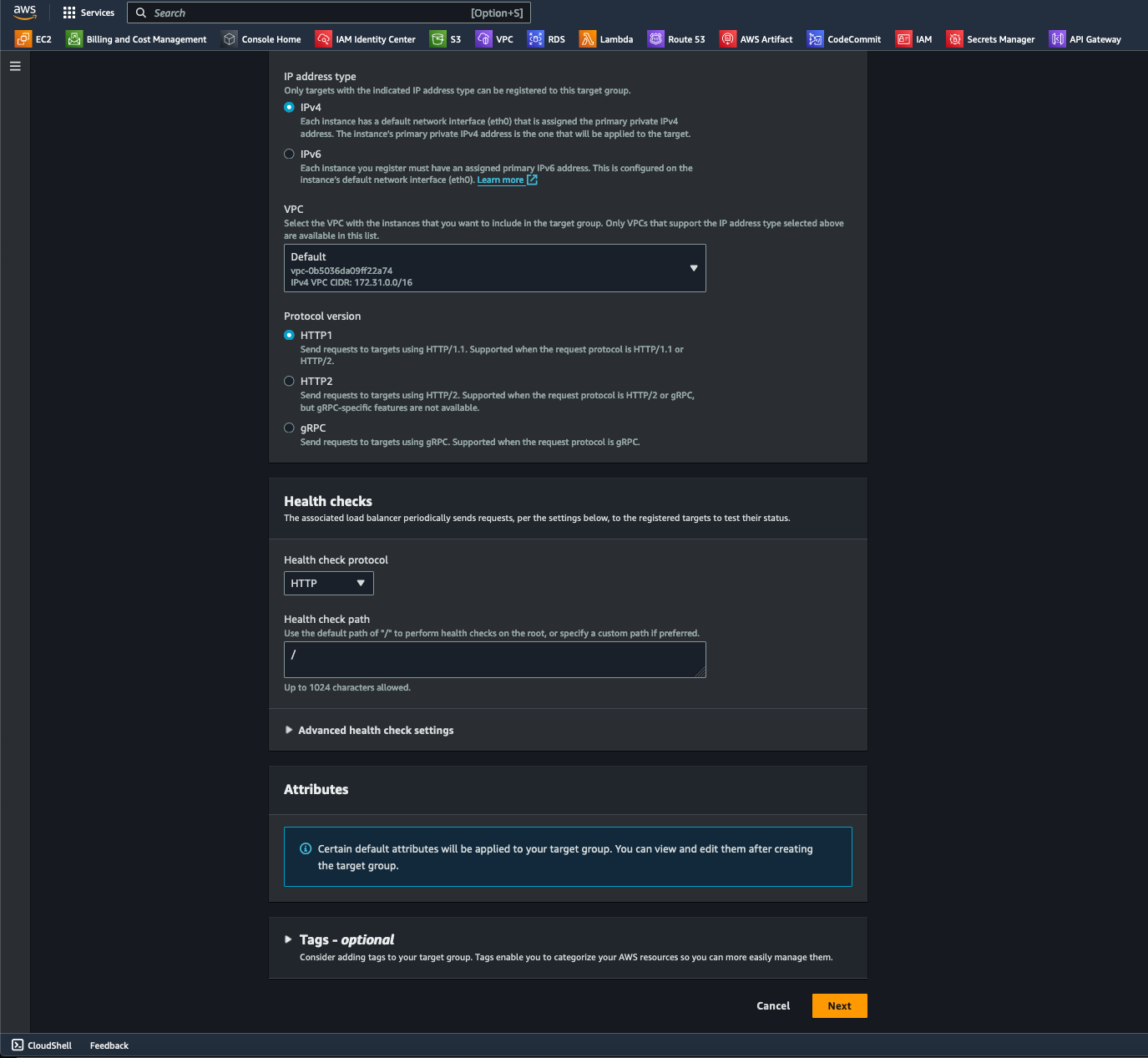
- I then added the instances to my target group by selecting the "include as pending review" button.
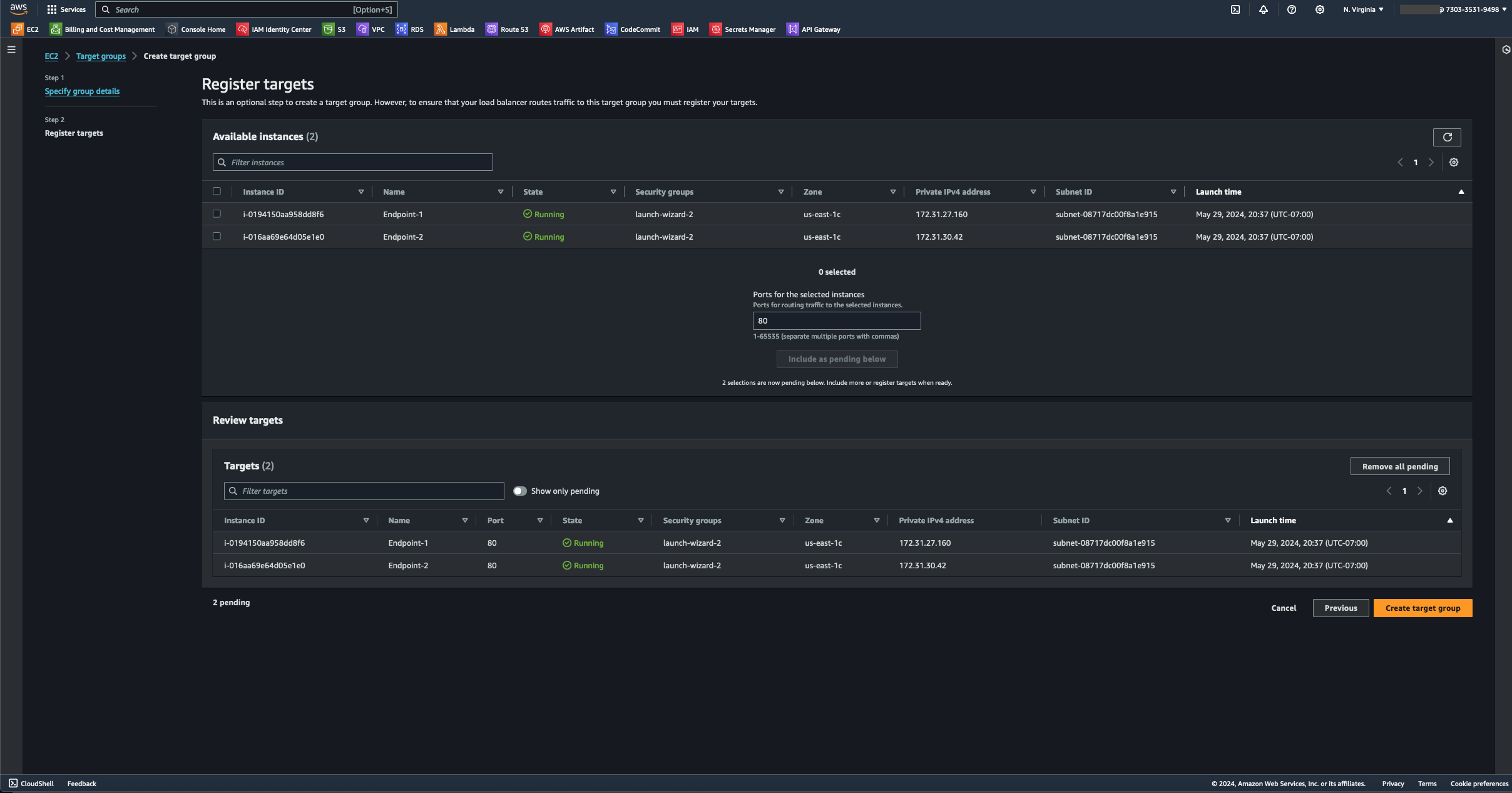
- Under Listeners and Routing, I selected the target group I created. I bypassed the Optimize with service integrations options because they are unnecessary for what I need to accomplish.
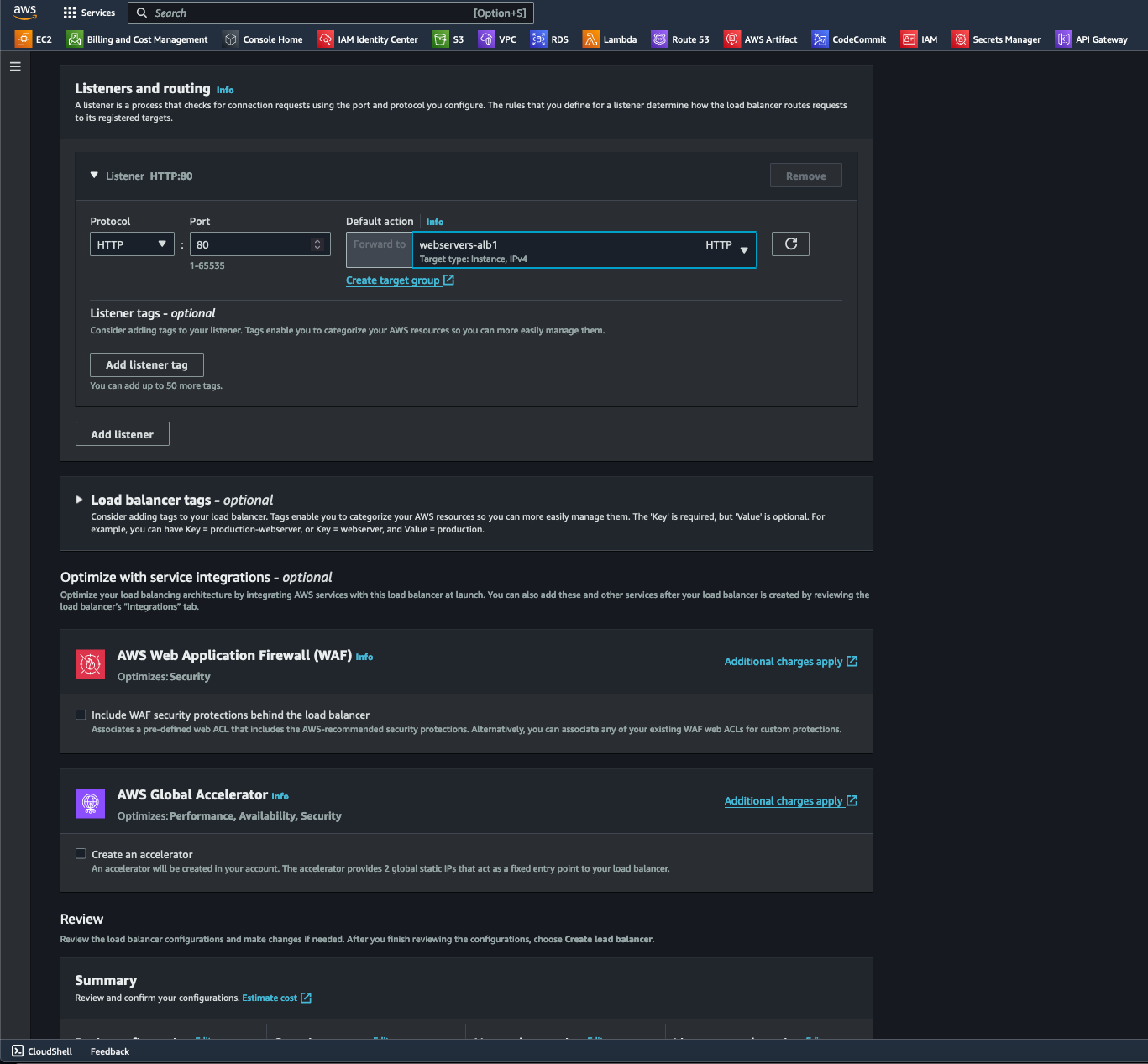
- To finally create the ALB, I selected the Create load balancer button at the bottom right of the page.
- Once my application load balancer transitioned to an active state, I copied its public IP address to verify its functionality later with a browser. Selecting the ALB and navigating under the Details tab exposes more information, including the ALB's public IP address.
- After pasting the public IP address of my application load balancer into a browser, I tested refreshing the browser multiple times to verify that the ALB switches between virtual servers under the target group, and it successfully did so. This proved that the ALB works by evenly distributing incoming network traffic.

- Under EC2/Target groups, I checked and verified that the instances under the target group are healthy. As a test, I stopped one virtual server from operating, causing the application load balancer to load only the healthy instance in the target group. This showed that the ALB demonstrated fault tolerance through instance redundancy, which concludes this test.